Imagine sending a message across the world and trusting it will arrive perfectly intact. That’s the magic of TCP, or Transmission Control Protocol – a core technology keeping the internet running smoothly. From emails to videos, TCP ensures that data travels reliably across networks, accurately and in the right order. In this post, we’ll dive into TCP’s essential role, uncovering how it powers the internet’s backbone and keeps our digital world connected. Ready to explore the engine behind online communication? Let’s get started!
Table of Contents
What is TCP/IP?
TCP and IP are two different communication protocols that complement each other’s functionality.
The Internet protocol or IP delivers (routes and addresses) data packets between a source (device or application) and their destination. It makes sure that those packets arrive at the right destination. It defines the rules and formats for applications and devices to communicate and exchange those data packets on a specific network or across different connected networks.
The transmission control protocol or TCP organizes data in a specific manner to protect them while exchanged between a client and a server. It’s a very used protocol on networks by all types of devices and applications. TCP protects data’s integrity from the sending and all the way to their delivery.
The development of these protocols (TCP/IP) happened in the 1970s. In that decade, the ARPANET became really popular, which motivated the creation of more networks to connect different organizations. Since those networks used a different protocol to send data back and forth, they could not communicate among them. The creation of a technology that could work as an intermediary to allow such communication became a need.
The combination of TCP and IP and its official adoption as the standard protocol -in 1983-for ARPANET (Internet’s predecessor) was the solution. No matter what other protocols networks used, if they supported TCP/IP, they could communicate with all the TCP/IP networks that existed.
The two technologies, TCP and IP, became the technical base for the modern Internet to operate and grow. Actually, here the word Internet emerged, meaning “an interconnected network of networks”.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
How does it work?
IP protocol works through different rules and resources, like the IP addresses. To connect to the Internet, domains and devices get a unique IP address to be identified and allowed to communicate (exchange data) with other connected devices.
Data travel across networks separated into pieces (packets). Every piece gets IP information (IP address) attached for routers to read it and send the packet to the correct destination. Once there, the way for those packets to be handle will depend on the kind of protocol (commonly TCP or UDP) combined with the IP to transport them.
IP is a connectionless protocol. All data packets are just addressed, routed, and delivered without existing acknowledgment from the destination to the source. This lack is resolved through the Transmission Control Protocol.
TCP secures the travel and delivery of data packets across networks through a specific process. To start, a connection between the source and the destination is required, even before the transmission of data begins. This, because TCP is a connection-oriented protocol. To work properly, it needs to guarantee this active connection until the sending and receiving of data get completed.
When the communication begins, TCP takes the sender’s messages and chops them into packets. To protect messages’ integrity, TCP numbers every packet. Then packets are ready to go to the IP layer for being transported. They will be dispatched to travel around different routers and gateways of the network to reach their destination. No matter all the packets are part of the same message, they can have different routes to arrive at the same destination.
Once they all hit their destination, TCP proceeds to re-build the message by putting all their pieces (packets) together again to make a proper delivery.
This ideal scenario can be affected if networks face issues. Data packets could get lost in transit, duplicated, or disordered. The advantage is TCP’s functionality can detect such problems and fix them. The protocol can ask the lost packets to be re-sent to organize them again in the correct order. In case messages can’t be delivered, this is reported to the sender (source).
As you see, the Internet is a packet-switched network. All data are chopped into packets that are dispatched through lots of different routes simultaneously. When they finally hit their destination, they get re-built by TCP. And IP is in charge of the packets to be sent to the correct destination.
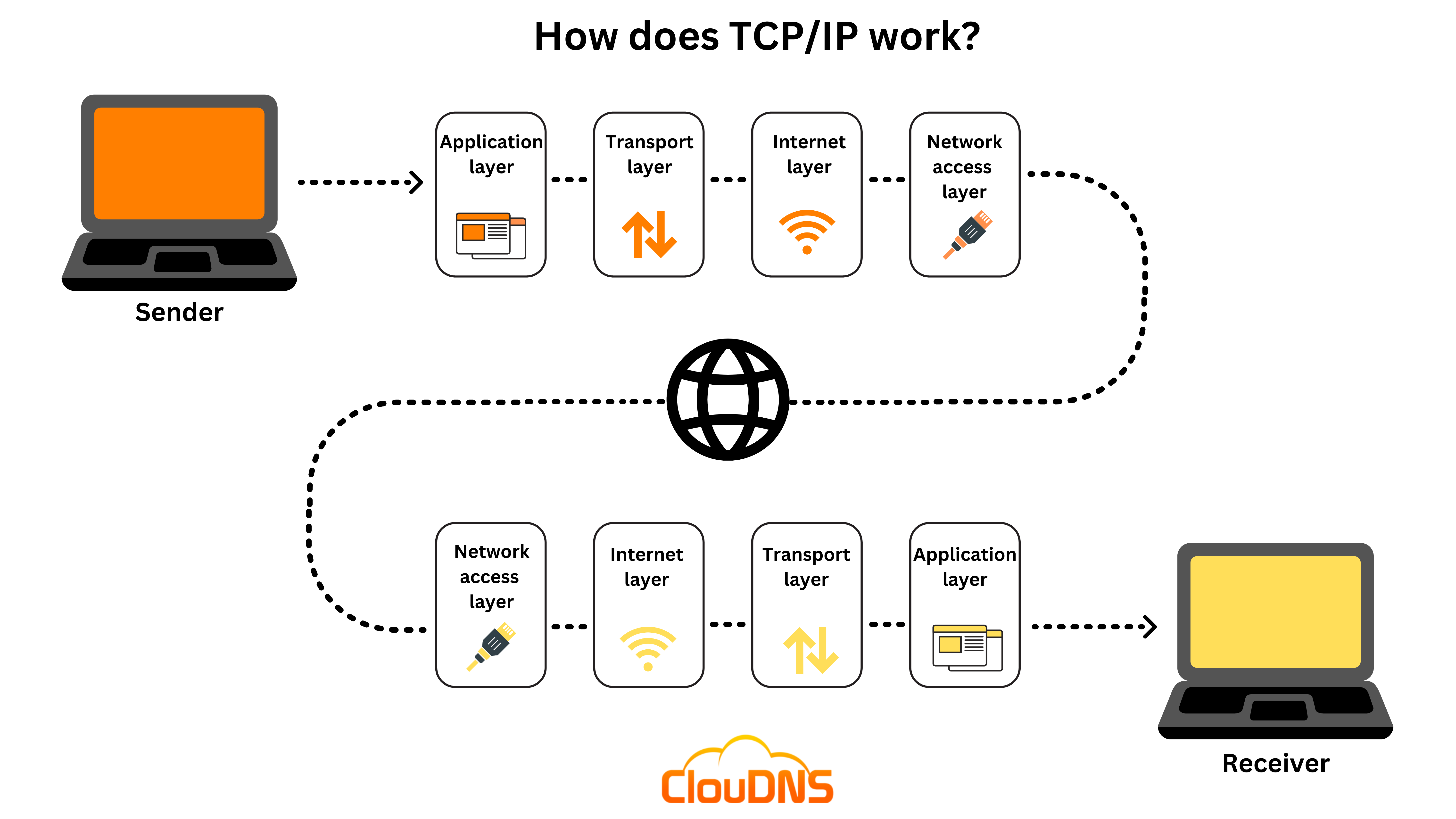
TCP/IP layers
TCP/IP’s most updated model includes the following four layers. All collaborate for the same purpose, the transmission of data.
- Application layer. This is the top layer, and it supplies an interface for applications and network services to communicate. It identifies participants involved in a communication, defines the access to the network’s resources, and the rules for application protocols and transport services interaction. Application layer includes all the higher-level protocols like DNS, HTTP, SSH, FTP, SNMP, SMTP, DHCP, etc.
- Transport layer. It defines the amount of data and the rate for transporting data correctly. It receives messages from the application layer, divides them into pieces, transports them, re-builds them following the proper sequence, and solves possible issues to guarantee their integrity and proper delivery. TCP operates in this layer.
- Internet layer. The internet layer, also known as the IP or network layer (not to be confused with the network access layer), is in charge of sending packets and ensuring that data is transferred as precisely as possible. As it controls the direction and pace of traffic, it is somewhat similar to a traffic controller on a road. Additionally, it supplies the procedural steps and functionalities for transferring data sequences. This layer’s protocols include IPv4, IPv6, ICMP, and ARP.
- Network access layer: The OSI model’s data link layer and physical layer are combined to form the network access layer. It outlines the process through which data is actually transferred over the network. It also covers how hardware components that physically interact with a network, such as twisted-pair copper wire, optical fiber, and coaxial cable, transmit data via optical or electrical means. The network access layer is the bottom layer in the TCP/IP model.
Understanding the TCP Handshake process
The TCP handshake process is the key to establishing a reliable connection between two devices. Known as the “three-way handshake,” this method ensures that both the sender and receiver are ready for communication before any data is transmitted. Here’s how it works step-by-step:
- SYN (Synchronization): The process begins when the client sends a SYN packet to the server, indicating a request to start communication. This packet also contains an initial sequence number, allowing the client to mark the starting point for data transmission.
- SYN-ACK (Acknowledgment of Synchronization): The server responds with a SYN-ACK packet, acknowledging the client’s request and including its own sequence number. This signals that the server is ready to receive data and has marked its starting point for tracking data segments.
- ACK (Final Acknowledgment): The client sends an ACK packet back to the server, acknowledging the server’s response. This final step completes the handshake, and a stable connection is established, allowing data exchange to begin.
What is the difference between TCP and IP?
TCP and IP are two different computer network protocols. Each function in the data transmission process distinguishes TCP (Transmission Control Protocol) from IP (Internet Protocol). Using IP, you may find out where data is sent (your device has an IP address). Once that IP address has been discovered, TCP guarantees accurate data delivery. The pair make up the TCP/IP protocol suite.
In other words, TCP sends and receives mail while IP sorts it. Other protocols, such as UDP (User Datagram Protocol), can transfer data within the IP system without the usage of TCP, even though the two protocols are typically regarded as a pair. But for TCP to deliver data, it needs an IP address. So another distinction between IP and TCP is this.
How to find your TCP/IP address?
To find your TCP/IP address, you can use simple methods for both your public and private IP addresses. Your public IP address, which identifies your device on the internet, can be easily found by searching “What is my IP address” in most search engines. This method displays the IP address assigned to your network by your Internet Service Provider (ISP).
For your private IP address, which is used within your local network, the process varies slightly depending on your device:
- On Windows: Open the Command Prompt and type ipconfig. Your IP address will be listed under the appropriate network adapter as the IPv4 Address.
- On macOS: Go to System Preferences, select Network, and choose the network you’re connected to. Your IP address will be displayed there.
- On Linux: Open the Terminal. You can find your IP address by typing ifconfig for older distributions or ip addr for newer ones. Your IP address will be listed under the relevant network interface.
- On mobile devices: Go to your Wi-Fi settings. Depending on your device, you may need to tap on the network you’re connected to see details like the IP address.
For TCP ports, determining which ports are being used by your device typically involves more technical steps. You can use network utilities or command-line tools to list active ports. These tools can help you identify which ports are open and in use, which is particularly useful for network troubleshooting or configuring firewall settings.
Remember, knowing your TCP/IP address is crucial for various network tasks, from setting up your home network to troubleshooting connectivity issues.
Are my data packets secure?
The answer is no. Why? When packets are sent between devices, they are highly susceptible to being intercepted by others. So, that’s why it’s better to utilize encryption and stay away from public Wi-Fi networks when transmitting messages that need to remain secret. But unfortunately, this is sometimes not enough, which is why you need to take other actions. Here’s what they are:
- Use Monitoring service
Systematically monitoring your network for any unusual activity. This reduces the exposure gap you have to cyberattacks. Additionally, TCP monitoring, which is a feature of the Monitoring service, uses a highly specialized protocol to examine connectivity and find communication problems on network machines. As a result, it can quickly identify issues and alert you.
- VPN
A VPN is a great way to guarantee that your data is securely encrypted and that your packets are safeguarded throughout network traffic. A VPN can be manually configured or purchased. Furthermore, VPN comes with numerous additional advantages. For example, website unblocking, location hiding, and restricting the pages you browse from being seen by your ISP (Internet Service Provider).
- Employ HTTPS protocols
Hypertext Transfer Protocol Secure (HTTPS), the prefix for encrypted websites, denotes the security of user activity there. Websites that begin with “HTTP” are unable to provide the same level of protection. Secure Sockets Layer (SSL) connections are indicated by the “s” in HTTPS, which stands for secure. Doing this guarantees, the data is encrypted before being delivered to a server. Therefore, to prevent packet sniffing, it is preferable only to visit websites that start with “HTTPS.”
HTTP vs HTTPS: Why every website needs HTTPS today
- Make use of Private DNS
Another important way to secure your data is to use Private DNS. Nowadays, using Public DNS has a lot of dangers. With Private DNS, you will be more secure against cyberattacks. Why? Because you can use Transport Layer Security (TLS) and Hypertext Transfer Protocol Secure (HTTPS). These protocols encrypt any DNS queries sent out, and DNS over these protocols is known as DoH (DNS over HTTPS) and DoT (DNS over TLS).
Advantages of TCP/IP
- It allows connecting different kinds of devices.
- It makes possible cross-platform communications among diverse networks.
- It supports different protocols for routing.
- It offers high possibilities of scalability. You can add networks without causing trouble.
- It supplies IP addresses to devices for identifying them.
- It’s independent of the operating system.
- It’s an open protocol. No one owns it. Everybody can use it.
- It facilitates reliable communication through data packet retransmission in case of loss, ensuring data integrity.
- It offers robust error detection and correction capabilities, enhancing data transmission reliability.
Disadvantages of TCP/IP
- To replace protocols on TCP/IP is not simple.
- It doesn’t define clearly the concepts of services, protocols, and interfaces. It can be difficult to assign a category to new technologies included in modern networks.
- It works for wide networks. It’s not suitable for small ones (PAN or LAN).
- Susceptible to security vulnerabilities if not properly secured, making encryption and other security measures essential.
TCP vs UDP
There are clear differences between the transmission control protocol (TCP) and User Datagram Protocol (UDP).
- TCP is connection-oriented, while UDP is connectionless. TCP requires an active connection to start and complete the data transmission, while UDP does not.
- TCP can recover lost packets by requiring retransmission. UDP can’t recover them.
- TCP is much slower than UDP because its process involves verification in almost every step. To guarantee the connection is active and the source ready to receive a message, to confirm delivery, etc. UDP only sends, avoiding those confirmation steps.
- TCP protects packets’ integrity efficiently. To protect this is not UDP’s strength. Its mechanism to check integrity (checksum) is less precise.
An Overview of TCP Monitoring vs UDP Monitoring
- TCP delivers ordered messages (by reassembling them based on a numerical sequence). UDP doesn’t offer this function.
- TCP guarantees the data delivery to their recipient. UDP doesn’t.
- TCP detects and fixes possible errors better. It also supplies confirmation of delivery or reports the problem if it’s not possible to deliver. The UDP’s mechanism for error detection (checksum) is simpler and limited. It doesn’t confirm or inform about the delivery.
- TCP’s speed doesn’t solve latency. UDP really does it.
- TCP doesn’t support broadcast, while UDP really does since it does not require response or confirmation.
- The efficiency of TCP makes it ideal for applications that demand full integrity of data, zero loss (HTTP, FTP, IMAP, SSH, SMTP).
- UDP works very well for applications that require high speed and can afford data loss. Think about real-time applications like live video streaming, voice-over IP or online gaming.
TCP vs HTTP
The Transmission Control Protocol (TCP) and the Hypertext Transfer Protocol (HTTP) also differ between them.
- TCP is used to set communication or a session between two machines (client and server). In contrast, HTTP is used for accessing data of webpages and accessing content (websites) from a web server. It’s a client-server protocol. Requests begin with the recipient, like a browser.
- TCP is a data transfer protocol. HTTP uses TCP for data transfer.
- TCP uses IP addresses, while HTTP uses hyperlinks, also known as URLs.
- TCP is connected-oriented, while HTTP is stateless but not sessionless.
- TCP needs authentication (TCP-AO). HTTP does not.
- TCP process involves a three-way handshake, and this takes some time. HTTP is one-way communication. TCP is slower than HTTP.
- TCP uses different ports (80, 8000, 8080, etc.). HTTP usually uses the 80 port.
Conclusion
There are different protocols, and understanding their potential is basic to choose the one that better suits your network’s needs. In many cases, these technologies compliment others. TCP, independently and combined with IP, is an efficient protocol with useful functionality for the Internet and networks in general. Try them and get the best out of them!






