As more and more of our data is being transferred over the Internet, protecting it from third-party interception is essential. DNS over TLS (DoT) and DNS over HTTPS (DoH) offer a secure and encrypted way to send DNS requests, so users can be sure their data is safe and secure. Let’s now learn how these protocols can help protect your data.
Table of Contents
What is DNS? Why does it need TLS or HTTPS?
DNS, short for Domain Name System, is a network protocol to translate human-readable domain names into numerical IP addresses that computers understand. DNS works just like old phone books, except that a DNS request is sent to the nearest name server to find the requested domain name’s corresponding IP address.
However, the issue is that DNS is an insecure network that can easily be intercepted, which can be a major security risk for users. This is why DNS needs TLS or HTTPS. They are encryption protocols that improve the security of DNS networks. TLS (Transport Layer Security) and HTTPS (Hypertext Transfer Protocol Secure) protect data transferred between computers, keeping the data private in case of interception. In addition, encryption ensures that data is not readable to parties not authorized to view it and is less vulnerable to data breaches. In short, TLS and HTTPS provide a much-needed safeguard to DNS requests and make sure that personal data remains safe and secure.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
How important is DNS request encryption?
Encrypting DNS requests is essential for data privacy and security. It hides the data associated with the request from malicious actors, preventing them from accessing it. This makes it significantly more difficult for third parties to view, track, or steal the data being transferred over the Internet. In addition, it eliminates the risk of DNS hijacking, which is when a cybercriminal reroutes a user’s web traffic from a legitimate website to a malicious website. In short, encrypting DNS requests helps users protect their data and ensure they browse securely.
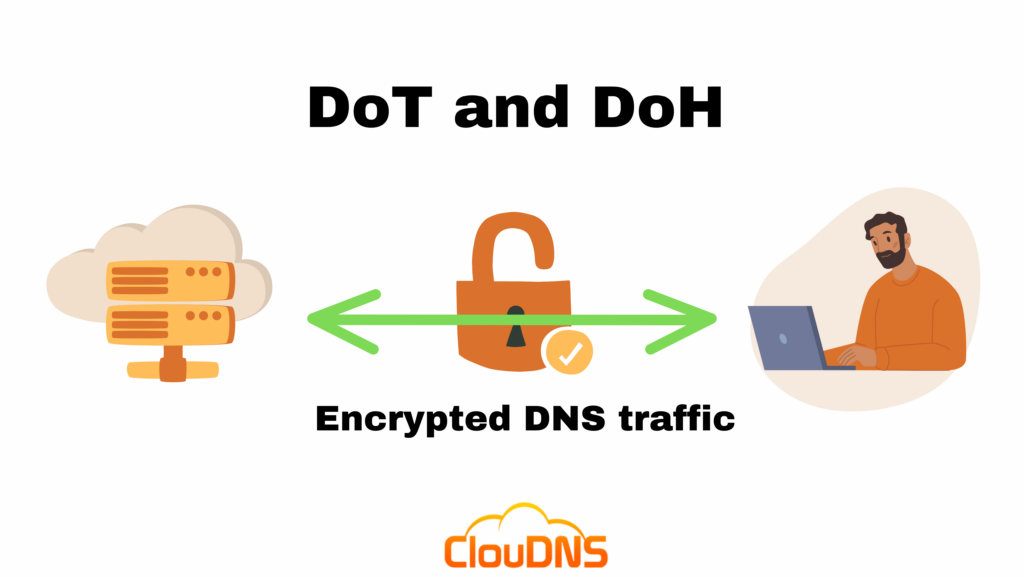
DNS over TLS (DoT) – What is it?
DNS over TLS (DoT) is a network protocol security measure designed to provide privacy and data integrity in communication between web browsers and DNS resolvers. It is an extension of the Transport Layer Security (TLS) protocol, also known as “SSL”. It is designed to help protect against malicious third parties accessing DNS request data transferred over the Internet in plain text. DoT adds an additional layer of TLS encryption on top of the User Datagram Protocol (UDP), which is associated with sending DNS queries.
DoT works by sending DNS requests over an encrypted TLS tunnel, adding a layer of security over an existing TLS connection. The data in the request is then encrypted with a unique key unique to the communication session. The DNS request and response are then sent as data packets encrypted and integrity-protected by the TLS protocol. This adds an extra layer of protection, allowing only the intended devices involved in a communication session to access the data. By doing so, DoT helps protect user data and prevents unauthorized third-party access, which can be especially useful when users use shared networks, such as public Wi-Fi.
Defining DNS over HTTPS (DoH)
DNS over HTTPS (DoH) is an alternative to DNS over TLS (DoT). DoH ensures DNS queries and responses are encrypted, and unlike DoT, it sends them via the HTTP or HTTP/2 protocols. From a network administrator’s perspective, this allows DNS traffic to look more like other HTTPS traffic – such as typical web interactions. Additionally, DoH provides a layer of security since attackers cannot forge or alter DNS traffic.
A key feature of DoH is that it hides the trustworthy source of the DNS requests from ISPs and other third parties monitoring web traffic. This makes it difficult for ISPs and other actors to track and collect data about users’ activities online, providing a layer of privacy for users. Additionally, DoH encrypts the entire DNS response, including the final IP address field, making it virtually impossible for third parties to access or view a user’s data.
So, what is the difference between DNS over TLS vs. DNS over HTTPS?
DNS over TLS and DNS over HTTPS are both secure and encrypted protocols for sending DNS requests over the Internet. The IETF (Internet Engineering Task Force) has outlined both protocols to provide a safe, reliable way of transferring DNS requests across the Internet.
The main difference is that DNS over TLS establishes the connection over TCP and layers over a secure TLS encryption and authentication protocol. At the same time, DNS over HTTPS uses the HTTPS and HTTP/2 protocol to establish the connection. Due to this difference, DNS over TLS has its own dedicated port, TCP Port 853, while DNS over HTTPS uses the standard HTTPS TCP port 443.
Another difference is the complexity of the encryption used. DoT creates an additional layer of TLS encryption over the underlying UDP used for DNS queries. DoH, on the other hand, uses HTTPS, which is more complex and secure. Additionally, DoH also encrypts the entire DNS response, including the final IP address field. This makes it virtually impossible for third parties to access or view a user’s data.
Finally, DoT is more widely used than DoH, but DoH is becoming more widely adopted due to its added security layer. DoT relies on DNS resolvers that support the protocol, but DoH can be used with any web browser supporting HTTPS. As more organizations, websites, and browsers adopt DoH, it will become the preferred method for secure DNS communication.
Which is better, DoT or DoH?
The answer to this depends on the company or even each IT security professional’s specific needs. However, there are a few facts that can be pointed out:
- From a network security standpoint, DoT is often preferred because it allows network administrators to monitor and block DNS queries. This helps them identify and stop potential malicious traffic.
- From a privacy perspective, DoH might be preferable since DNS queries are hidden within the larger flow of HTTPS traffic. This provides users with more privacy but makes it harder for network administrators to block malicious traffic, as doing so would require blocking all other HTTPS traffic as well.
Private DNS server and its relation with DoT and DoH
The aim of Private DNS server is to resolve external DNS queries, such as lookups for Internet web pages or other resources on the web. Therefore, any data sent back and forth between the Private DNS server and the other DNS servers must be secure to prevent any snooping or manipulation of the data. This is where DoT and DoH come in. By using them, the data sent between the Private DNS server and the other DNS servers is encrypted and protected from potential attackers, ensuring the data remains private and tamper-free.
Challenges in implementation DoT and DoH
- Compatibility Issues: Some older systems and applications may not support DoT or DoH, leading to compatibility challenges.
- Configuration Complexity: Properly configuring DoT or DoH can be complex, especially in environments with existing security measures.
- Mixed Content Handling: Websites that load over HTTPS but make DNS requests over unencrypted channels can present challenges in environments where DoT or DoH is enforced.
Guides for setting up DoT and DoH
To enhance your online privacy and security, follow these setup and configuration guidelines on various operating systems:
- Windows: Use the Network Settings to specify a preferred DNS server that supports DoT or DoH. Third-party applications can also enable DoT/DoH on systems where native support is lacking.
- macOS: In Network Preferences, you can configure DNS settings to use servers that support encryption. Several apps are available to automate this process.
- Linux: Depending on the distribution, you can edit the resolv.conf file or use systemd-resolved to configure DoT or DoH.
- Android: Recent versions allow you to specify a Private DNS provider in the network settings, enabling DoT by default.
- iOS: Use a DNS profile or a third-party app to configure DoT or DoH, as iOS does not natively support changing DNS settings directly for cellular networks.
The role of DNS Encryption in IoT security
IoT devices rely heavily on DNS for communication, making them vulnerable to attacks like DNS spoofing and man-in-the-middle (MitM). DNS encryption, through protocols like DoT and DoH, is crucial for securing these communications.
- Preventing DNS Spoofing: Encryption ensures devices connect only to legitimate servers.
- Mitigating MitM Attacks: Encrypted DNS traffic blocks attackers from intercepting or tampering with queries.
- Enhancing Privacy: Protects sensitive IoT data from being monitored or tracked.
- Securing Public Networks: Shields IoT devices operating on shared or public networks.
By securing DNS traffic, DNS encryption strengthens IoT security and protects against vulnerabilities inherent to many IoT devices.
What’s the difference between DoT/DoH and VPNs?
DNS over TLS (DoT) and DNS over HTTPS (DoH) are protocols designed to encrypt DNS queries, providing enhanced privacy and security when resolving domain names to IP addresses. They primarily focus on securing the DNS lookup process and preventing potential eavesdropping or manipulation of DNS traffic.
On the other hand, Virtual Private Networks (VPNs) create a secure, encrypted tunnel between your device and a remote server operated by the VPN provider. This tunnel encrypts all the data passing through it, not just DNS queries. VPNs are used to secure all internet traffic, including web browsing, app usage, and other online activities, from potential interception or monitoring by third parties, such as hackers, government agencies, or Internet Service Providers (ISPs). Alternatively, SOCKS5 proxies provide a way to mask IP addresses and bypass certain restrictions, but they do not encrypt traffic, leaving data exposed to potential interception.
In summary, while DoT/DoH focus specifically on encrypting DNS queries to protect against DNS-related threats, VPNs encrypt all internet traffic to provide comprehensive online privacy and security.
Conclusion
With the growing trend of data privacy and the desire for quicker browsing speeds, DoT and DoH add an extra layer of security and speed to your network. Therefore, it’s time to take control of your safety and privacy by making the change – try DoT and DoH and see how they can help make the internet a safer place.