How does OSI Application layer 7 DDoS attack work?
As cyber threats evolve, Distributed Denial of Service (DDoS) attacks have become more...
Getting Started with DNS Prefetch on Your Website
In the ever-competitive landscape of web performance, milliseconds matter. Whether you’re optimizing for Core Web Vitals, reducing...
Webhook Basics: Automate with Ease
Webhook is an amazing technology that facilitates seamless communication between different applications and services. It offers an...
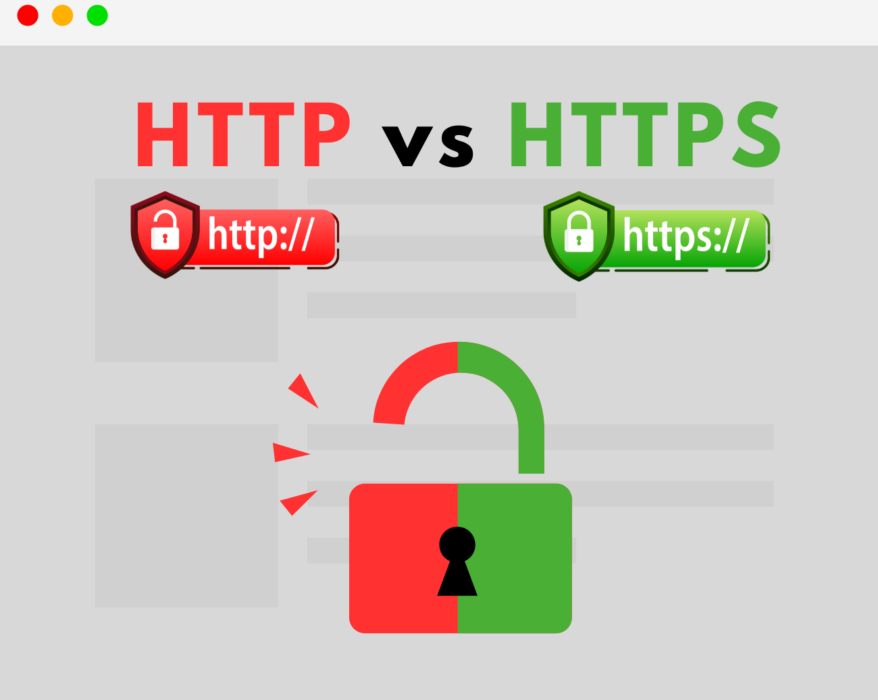
HTTP vs HTTPS: Why every website needs HTTPS today
In today’s digital age, securing information online has become more important than ever. One...
Understanding the HTTP status codes
Any now and then, when we are browsing the internet, we get one of those – error 500 or error 404. What does this number mean? How many...
FTP vs HTTP: Understanding the Key Differences
Today we will see what exactly is FTP (File Transfer Protocol) and how does it compare to the newer protocol called HTTP (Hypertext...
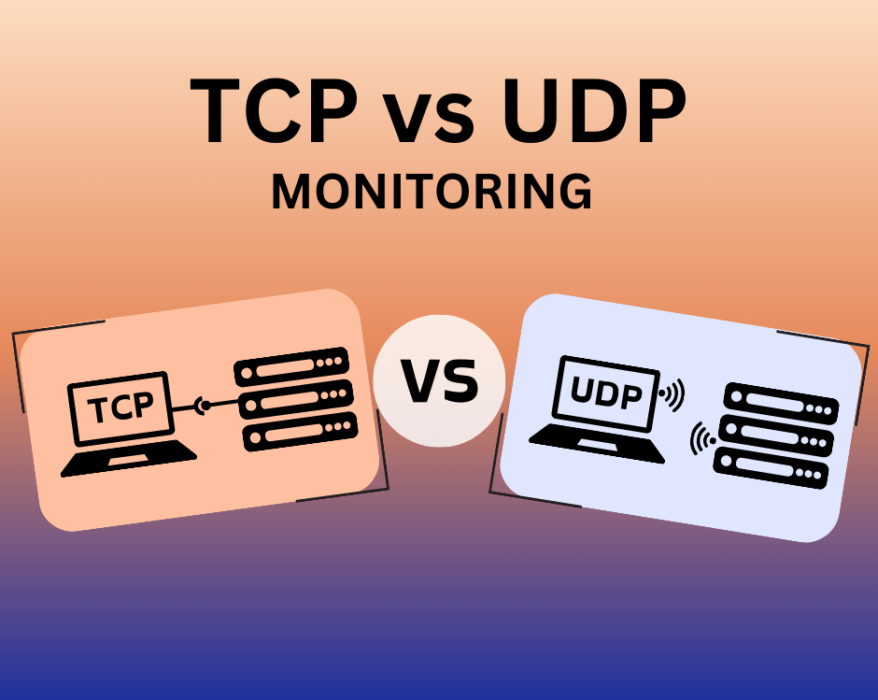
Comprehensive Guide on TCP Monitoring vs. UDP Monitoring
Why does the battle between TCP monitoring vs UDP monitoring matter in the world of network...
How do OSI Model layers work in computer networking?
In the vast realm of networking, the Open Systems Interconnection (OSI) Model stands as one of the most fundamental frameworks. It is the...
TCPdump for Beginners: What It Is, How to Install, and Key Commands
TCPdump is a powerful command-line tool for analyzing network traffic in real-time, making it indispensable for network administrators and...
TCP (Transmission Control Protocol) – What is it, and how does it work?
Imagine sending a message across the world and trusting it will arrive perfectly intact. That’s...