Imagine a tech gremlin relentlessly hammering at the door of a server, bombarding it with so many requests that it can’t keep up and serve its genuine users. This is no figment of imagination, but a very real cyber threat known as a SYN flood attack. It’s an insidious assault that takes advantage of the basic ‘handshake’ protocol computers use to communicate and then leaves the server overwhelmed and powerless. However, fear not! The dynamic world of cybersecurity presents a host of savvy solutions to guard against such attacks, making this dark digital menace completely manageable.
Table of Contents
SYN flood attack: Origin and Basics
In the 1990s, a man named Wietse Venema explained a certain attack method in-depth. On its surface, the concept seems innocuous enough. In a network protocol, namely TCP, a three-way handshake commences communication. Imagine this as a modern chivalry ritual between your computer and the server you want to engage with.
- You send a SYN (synchronize) packet: “Hi, can we chat?“
- Server sends back SYN-ACK (acknowledgment): “Sure, let’s talk.“
- You finish with an ACK: “Cool, let’s get started.“
What SYN flood attack is?
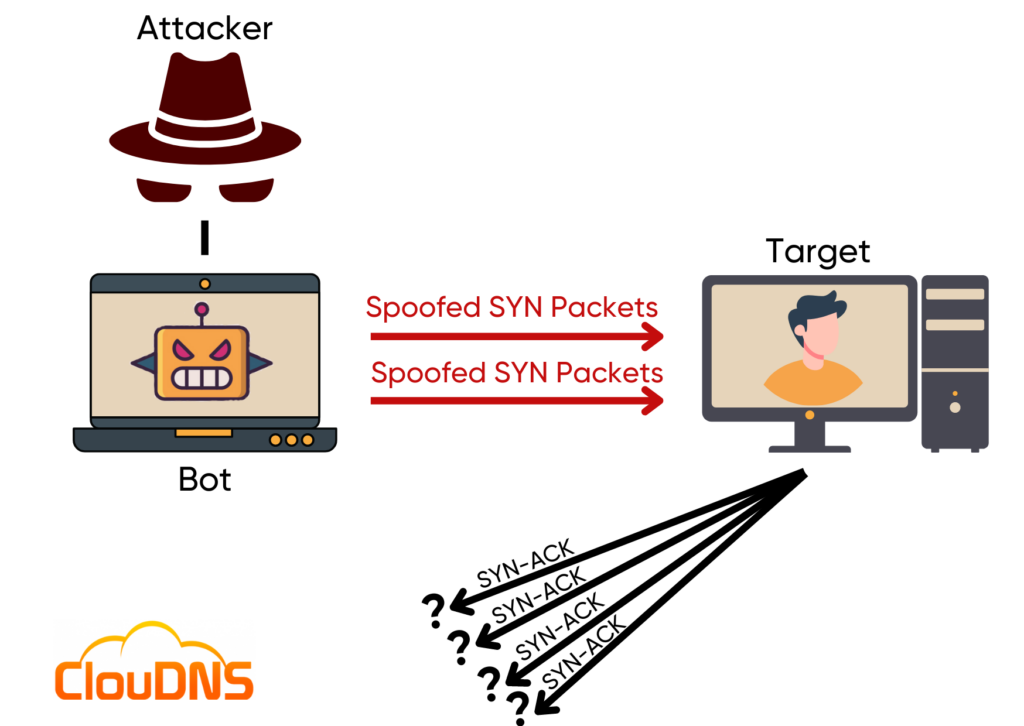
Broadly speaking, a SYN flood attack, also referred to as a TCP/IP-based attack, is a type of Denial of Service (DDoS) attack on a system. It might be compared to an irritating prankster continuously dialing a business phone to keep the line busy and prevent legitimate callers from reaching the establishment. The attacker here sends a flood of SYN requests from either a single or multiple spoofed IP addresses to a server with the malicious intent to halt the server’s functionality to process new incoming service requests. As the server gets trapped in a vicious cycle of responding to these inexistent or half-open connections, it can lead to crashing or becoming unavailable to legitimate users.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
How does it work?
The mechanics of a SYN flood operate in a methodical sequence of steps that exploit the TCP handshake protocol. Let’s break it down for clarity:
Step 1: Identifying the Target
The attacker first picks out the target server. Usually, they’re gunning for a specific service, like a website or an application hosted on that server.
Step 2: Initiating SYN Requests
Here, the attacker commences the mischief by generating a multitude of SYN packets. Each of these SYN packets asks the server, in essence, for permission to establish a connection.
Step 3: Half-Open Connections
Upon receiving a SYN request, the server reciprocates with a SYN-ACK packet and moves the corresponding request to a backlog queue. This places the connection in a “half-open” state, awaiting the client’s final ACK for completion.
Step 4: Server Response
At this juncture, the attacker ghosts the server, never sending the final ACK to complete the handshake. Consequently, the server’s backlog queue starts brimming with incomplete handshakes.
Step 5: Resource Exhaustion
With each half-open connection, the server allocates a chunk of its resources. As these incomplete connections accrue, the server begins to hit its limit on resources.
Step 6: Denial of Service
At this point, the server becomes unable to accept any new connections. Legitimate users trying to connect encounter timeouts or failures, achieving the attacker’s endgame of denying service.
Types of SYN Flood Attacks
SYN flood attacks can take on multiple forms, each with its own level of complexity and associated risks:
- Direct Attack: In this type of attack, the attacker does not hide their IP address, meaning that all traffic comes from a single source. This makes it relatively easier for network administrators to identify and block the attack by filtering the IP address. However, direct attacks can still overwhelm a server, especially if they come from high-capacity sources.
- Spoofed Attack: Here, the attacker sends SYN requests using spoofed IP addresses, making it difficult to track the origin of the traffic. The server tries to send SYN-ACK packets to non-existent or unreachable IPs, leaving the connections open and slowly exhausting server resources. Spoofing adds an extra layer of complexity, making it harder to mitigate, as simply blocking the traffic source won’t solve the problem.
- Distributed Attack (DDoS): In a distributed SYN flood attack, the attacker uses a botnet – a network of compromised devices – to send SYN requests from various IP addresses. This creates massive amounts of traffic from multiple sources, overwhelming the server and making it extremely difficult to pinpoint and block the attack. This method was infamously used by the Mirai botnet, which leveraged IoT devices to launch one of the largest DDoS attacks in history.
Common signs you’re under a SYN flood attack
SYN flood attacks can sometimes be subtle at the start, but there are distinct signs that indicate an active threat. Identifying these early can help minimize damage:
- Sudden spike in SYN packets without corresponding ACKs in network logs.
- Service unavailability or timeouts for legitimate users trying to establish a connection.
- High CPU usage or memory exhaustion on the server, especially in the networking stack.
- Backlog overflow warnings in system or firewall logs.
Real-time traffic analysis tools and anomaly detection systems can help you catch these symptoms before the server becomes fully compromised.
Ways to mitigate the SYN flood attack
Ah, but there’s hope! Multiple strategies can serve as lifelines in mitigating the fallout from a SYN flood.
SYN cookies
Implementing SYN cookies proves useful in minimizing risk. When deployed, the server doesn’t allocate resources right away for a new SYN request. Rather, it converts the connection into a unique cryptographic cookie. Only when the handshake gets completed does the server expend resources, reducing vulnerability to attacks.
Rate limiting
Another solid tactic involves imposing rate limiting on incoming SYN packets. By setting a strict threshold for the number of allowable new connections per unit of time, the server can effectively nip malicious flood attempts in the bud.
DDoS Protection
Incorporating DDoS protection is an advanced, indispensable strategy. These specialized solutions not only defend against SYN flood attacks but also guard against a broader range of DDoS threats. DDoS protection services usually feature large traffic scrubbing networks that can sift through immense volumes of data, allowing legitimate traffic through while blocking malicious requests.
Anycast DNS
Anycast DNS serves as another invaluable layer of defense. By distributing incoming traffic across multiple data centers (PoPs), it minimizes the load on any single server. This distribution can effectively dilute a SYN flood attack, rendering it far less potent. Anycast DNS is especially beneficial when used in conjunction with DDoS protection services, providing an additional layer of robust, scalable defense.
Robust Load balancers
High-capacity load balancers can significantly improve your system’s capacity to manage an enormous volume of connection requests. In turn, this can enhance your network’s ability to resist SYN flood attacks.
Monitoring services
Real-time Monitoring services track and scrutinize network patterns, activities, and performance, enabling the early detection of potential threats or attacks. These services can monitor server health, network performance, and traffic patterns, thereby identifying and alerting about possible anomalies that might indicate a SYN flood attack.
Firewall rules
Tweaking firewall configurations can also be invaluable. For instance, you can set rules to block incoming requests from a specific IP address if it exceeds a set number of SYN requests within a short timeframe.
Suggested article: Router vs firewall
Consequences of non-protection
- Service disruption: SYN flood attacks can result in service disruption or downtime, as the targeted server becomes overwhelmed and unable to handle legitimate requests.
- Financial loss: Downtime can lead to financial losses for businesses, especially e-commerce websites, online services, and organizations heavily reliant on internet connectivity.
- Reputation damage: Frequent DDoS attacks, including SYN floods, can tarnish a company’s reputation, eroding trust and customer confidence.
- Security overhaul costs: Post-attack, merely patching vulnerabilities won’t suffice. A complete revamp of security protocols becomes vital, often draining both time and financial resources.
Conclusion
In a world increasingly reliant on digital technology, understanding and defending against threats like SYN flood attacks is crucial. While they are a potent threat, solutions such as SYN cookies and robust load balancers offer effective means of mitigation. In essence, maintaining cybersecurity is not just a good idea, but a necessity in today’s digital landscape.