Email forwards – what are they and how to use them?
Can you guess what email forwards do? Yes, it is very simple, they redirect emails from one mailbox...
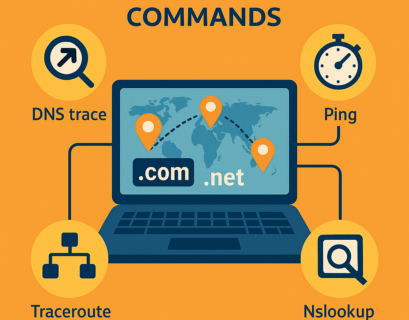
Тools – DNS trace, Ping, Traceroute, Nslookup, Reverse lookup
Navigating the world of DNS and network management can often feel like a complex puzzle, especially when things don’t work as...
DNS zone transfer and zone file (Updated)
We have already covered the bases of DNS, so you know what it is and how does it work. This article will help you understand one of...
Webhook Basics: Automate with Ease
Webhook is an amazing technology that facilitates seamless communication between different...
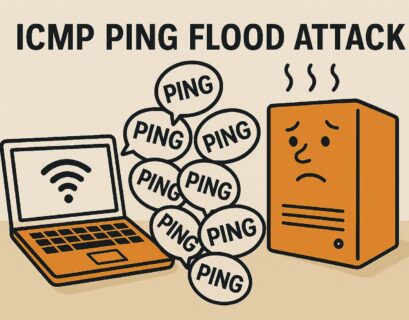
What is ICMP (Internet Control Message Protocol)?
The ICMP (Internet Control Message Protocol) is a network layer protocol and also a supporting protocol in the Internet protocol suite. It...
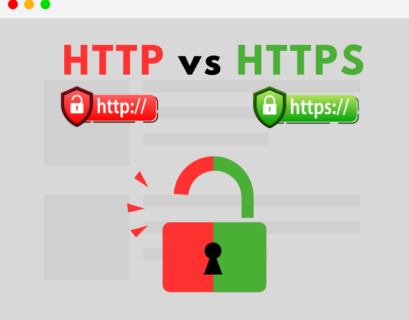
HTTP vs HTTPS: Why every website needs HTTPS today
In today’s digital age, securing information online has become more important than ever. One key aspect of online security revolves...
What are 301 and 302 Redirects and how to use them?
In the realm of website management and search engine optimization (SEO), proper redirection plays a...
10 Most used DIG commands
DIG commands offer a vast amount of functionalities and different options. So, it is not a surprise that they are some of the most popular...
Why does DNS use UDP?
If you have ever wondered why DNS primarily relies on UDP (User Datagram Protocol) instead of other...