You may have heard about SSH due to the fact it is often mentioned for anything associated with cyber security. It appears as a very interesting topic. So, let’s explain more about it and how it actually works!
Table of Contents
SSH meaning
The short SSH stands for Secure Shell or Secure Socket Shell. It represents a well-known network protocol that provides regular users and, more precisely, system administrators with a secure method to access a device over an secured network.
In addition, SSH even refers to the suite of utilities that use the SSH protocol. Secure Shell allows the implementation of robust password authentication and public key authentication, plus encrypted data transmissions among two devices connecting over an open network, like the Internet.
Due to the fact it delivers strong encryption, Secure Shell is a popular tool used globally. That is especially helpful for network administrators that manage systems and applications remotely. It allows them to log in to another computer over a network, execute commands and move files from one device to another.
As we mentioned, SSH refers both to the cryptographic network protocol and the suite of utilities that use that protocol. SSH operates involving the client-server model. It connects a Secure Shell user application – the end where the session is displayed, and an SSH server – the end where the session runs. The use of Secure Shell commonly involves support for application protocols utilized for terminal emulation or file transfers. This protocol is also implemented for making safe tunnels for other application protocols, for instance, to run X Window System graphical sessions remotely securely.
A brief history of SSH
SSH was developed back in 1995 by Tatu Ylönen, who was, at the time, a researcher at the Helsinki University of Technology. The primary motivation for creating the protocol was to prevent password-sniffing attacks. The first version of the protocol, currently known as SSH-1, had the goal of replacing not-so-reliable protocols like rsh, rlogin, and Telnet. It was freeware in the beginning, and not long after became proprietary software.
Without a doubt, Tatu Ylönen’s protocol was a well-known and widespread tool used all over the world. Therefore, the Internet Engineering Task Force (IETF) formed a group of specialists in order to develop a successor to the protocol. That way, in 2006, SSH-2 was introduced and became a new standard, featuring security improvements like the Diffie-Helman key exchange.
The open-source community, desiring the availability of a free software version, created an SSH protocol version based on version 1.2.12 of SSH-1, known as OSSH. Later, The OpenBSD developers forked OSSH to create OpenSSH, which is the most famous SSH implementation in the world today. However, OpenSSH supports only SSH-2, and the support for SSH-1 has been stopped.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
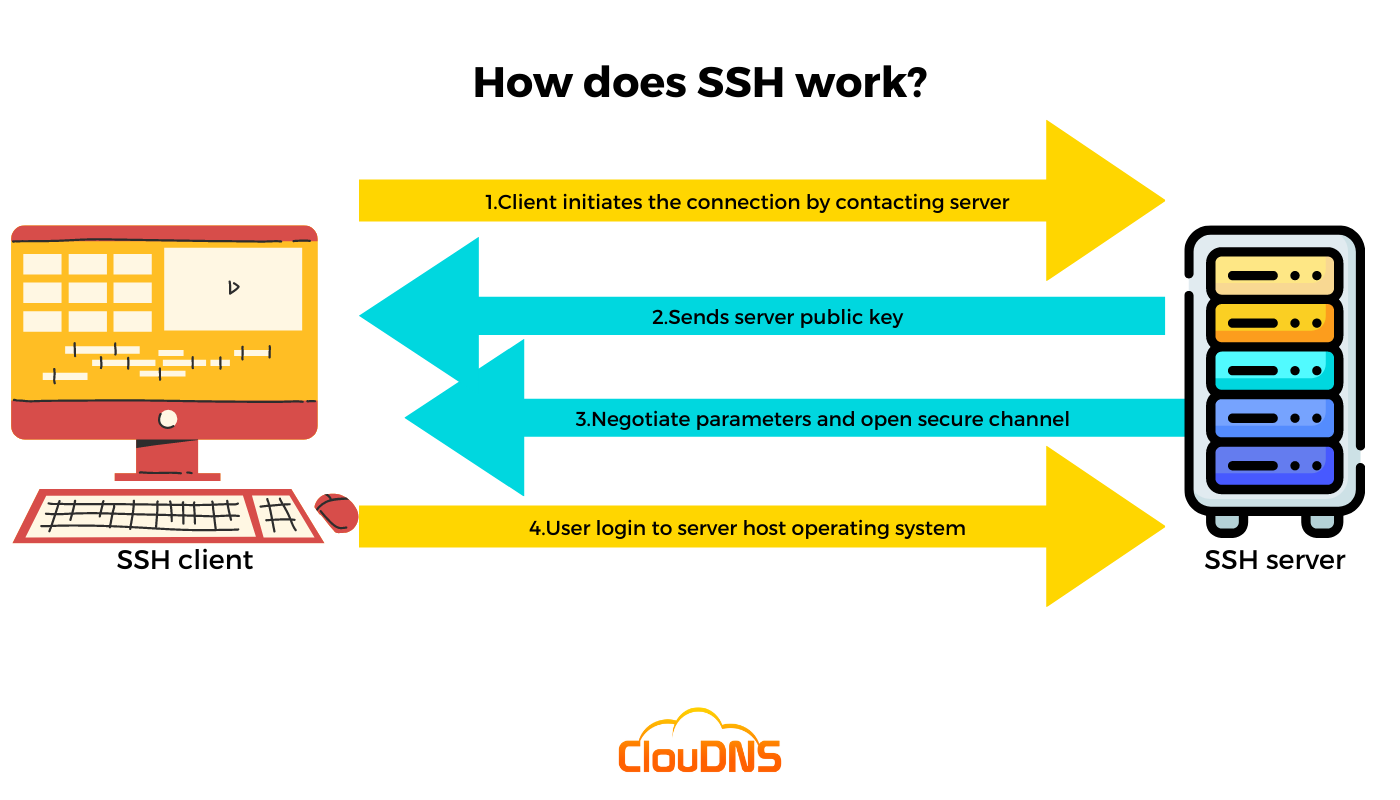
How does it work?
Secure Shell was developed mainly to replace not-safe terminal emulation or login programs, like Telnet, rlogin (remote login), and rsh (remote shell). It allows the same opportunities – logging in to and running terminal sessions on distant systems. Also, SSH is able to replace file transfer programs, like File Transfer Protocol (FTP) and rcp (remote copy).
However, in most cases, it is utilized to connect to a remote host for a terminal session. Here is the structure of the command that the user issues using the terminal:
ssh [username]@[server_ip_or_hostname]
Example: ssh username@SSHserver.example.com
With this command, the client is able to try to connect to the server (server.example.com) with its ID username. Suppose this is the first attempt for a connection between the local host and the server. In that case, the user will receive the remote host’s public key fingerprint and be prompted to connect, even though there has been no previous connection:
The authenticity of host ‘test.example.com (192.168.0.100)’ cannot be established.
EdDSA key fingerprint is SHA256:xxImLADIinZpfy/etR8GOoXzCkbaHasaqLPS9ZOWKW4.
Are you sure you want to continue connecting (yes/no)?
Once you answer yes, the session continues, and the host key is saved in a file in the local system. The file is hidden in a directory in the user’s home directory. Once this file is established, the client system is able to connect directly next time without the need for any approvals. That way, the host key verifies the connection.
What is it used for?
It is not a surprise that Secure Shell is widely implemented in data centers in order to deliver safe management and remote access to different resources, software patches, and updates. In addition, the protocol allows secure router management and server hardware supervision.
Due to the fact it is super easy to use, robust and has various features, Secure Shell finds its application in many cases. Some of them are the following:
- Connect to a remote host.
- Using a Virtual Private Network.
- Back up, copy, and mirror files utilizing SFTP.
- Mapping a user’s port to the server’s port to secure TCP/IP
- Tunneling sensitive information via a protected channel.
- Forwarding X Window System from the server to clients.
Besides, SSH keys are commonly used in automating server access via passwordless login, configuration management, and backup.
How to use it?
The connection with an SSH server is achieved by utilizing an SSH client. The majority of Unix-based and Unix-like operating systems (OS) include already installed daemon and the client. So, on these systems, you can find the SSH client in the terminal.
The user has to issue the ssh command with the username and the server address or hostname in order to connect to a remote host:
ssh [username]@[server_ip_or_hostname]
*If a username for SSH is not specified, the connection uses the currently logged-in user.
OpenSSH client and server are offered in version 1709 for Windows 10. So for earlier versions of Windows, tools such as PuTTY were used to establish an SSH connection because they do not offer Secure Schell as a feature. PuTTY is an SSH client with a GUI for Secure Shell and Telnet.
SSH port
Achieving successful communication with Secure Shell requires a port to connect and start. For that reason, usually, all the contacts are performed using SSH port number 22. It is possible to change the number with any other available port number.
However, when the user runs the command and wants to start the communication between two devices over the network, by default, it uses port 22.
In case you want to carry sensitive information that needs to be protected, it is best to switch the usual port number with another one. That helps you avoid any potential brute-force attack. Due to the fact everybody knows about the default port 22, it is not the most secure option. It is most prone to malicious attempts, and criminals use it to steal the transferred information.
SSH Authentication Methods
Secure Shell supports various authentication methods to ensure secure connections:
- Password Authentication: The simplest method, where users authenticate with a username and password. While convenient, it is not recommended for environments demanding high security.
- Public Key Authentication: A more secure method using cryptographic key pairs (public and private keys). The private key remains with the user, and the public key is placed on the server. This method is highly secure and ideal for automation and passwordless login.
- Two-Factor Authentication (2FA): Secure Shell can be configured to use 2FA, adding an extra layer of security by requiring a one-time password (OTP) in addition to the private key or password.
Choosing the right authentication method can significantly increase the security of your SSH connections.
Types of SSH Encryption
Secure Shell employs several encryption methods to secure communication between client and server. These include:
- Symmetric encryption: A single, shared key used for both encryption and decryption. This method is fast and ideal for secure sessions.
- Asymmetric encryption: Involves a pair of keys (public and private), where data encrypted with one can only be decrypted by the other. This is used to exchange keys securely at the beginning of a session.
- Hashing: Verifies data integrity using a Message Authentication Code (MAC) or Hashed Message Authentication Code (HMAC), ensuring the data hasn’t been tampered with. This is particularly useful for preventing man-in-the-middle attacks.
SSH Keys
SSH keys consist of a pair of cryptographic keys: a private key, which is kept secret by the user, and a public key, which is shared with the server. When attempting to log in, the server checks if the client has the corresponding private key, which verifies the user’s identity without needing a password.
- Generating SSH Keys: Users can generate SSH keys using tools like ssh-keygen in the terminal. The keys are stored in the user’s local machine, with the public key placed on the server for access.
- SSH Key Pairs: Each SSH key pair consists of a public key (placed on the server) and a private key (kept on the client machine). This key-based authentication method greatly reduces the risk of brute-force attacks compared to traditional passwords.
- Passphrase Protection: SSH private keys can be further secured with a passphrase, adding an additional layer of protection in case the private key is compromised.
- SSH Key Management: Proper key management is critical, especially in large environments. Mismanagement, like sharing keys insecurely, can lead to unauthorized access.
By implementing SSH key authentication, you increase both security and efficiency, particularly in environments requiring automated or frequent access to remote systems.
SSH Keys vs Passwords
SSH keys are generally much more secure than passwords for authentication. Password-based authentication relies on the user creating a strong, unique password. However, weak or reused passwords are vulnerable to brute-force attacks, where attackers try many possible combinations to guess the password. Even strong passwords can be at risk if users don’t change them regularly or if attackers use advanced methods.
In contrast, SSH keys use a pair of cryptographic keys — one public and one private. The private key is stored securely on the user’s computer, while the public key is placed on the server. The server only grants access when the user can prove they have the matching private key. This method is far more secure because even if an attacker obtains the public key, they cannot log in without the private key.
SSH keys also allow for passwordless login, making it convenient while still maintaining high security. Users can optionally protect the private key with a passphrase for added security.
How secure is SSH?
Secure Shell is considered to be one of the highly secure protocols. Yet, the human factor is highly important in order to preserve the safety of such connections. Here are several potential vulnerabilities in Secure Shell connections:
- Brute-force attacks on SSH servers are very popular. Criminals try to connect to as many SSH servers as possible utilizing typical usernames and passwords.
- SSH keys are the preferred security authentication method over passwords. Yet, bad SSH key management can significantly threaten organizations whose sensitive data relies on holding the keys secret. Additionally, their misusage can supply cyber criminals access to confidential data, like accounts, resources, databases, routers, payment systems, etc.
- Exposed SSH ports are also a potential security vulnerability. There are malware programs that attack IoT devices with ports exposed. That way, they become a backdoor entry to the local network.
What is SSH tunneling?
SSH tunneling, also known as SSH port forwarding, is a feature of SSH that extends its capabilities beyond remote access. With SSH tunneling, you can create encrypted connections between two devices, typically a local client and a remote server, to transfer data securely. This data can include sensitive files, database connections, or web traffic. It is also particularly useful when you need to access services on a remote server that might not be directly accessible from your local network.
There are two primary types of SSH tunneling: local and remote.
- Local SSH Tunneling: In a local SSH tunnel, you create an encrypted connection from your local machine to a remote server. This connection is used to securely forward traffic from your local machine to the remote server. It is often used to access services on the remote server that are not directly accessible from your local network. For example, you could tunnel your web browser’s traffic through the SSH connection to access a web service on the remote server.
- Remote SSH Tunneling: Remote SSH tunneling involves creating a secure connection from a remote server to your local machine. This is useful when you want to allow a service on the remote server to access resources on your local network securely. For example, you could use remote SSH tunneling to allow a remote database server to connect to a database on your local network.
Telnet vs SSH
When talking about remote connectivity, the two protocols that are often used are SSH and Telnet. While both serve the purpose of allowing users to access remote systems, they differ significantly in terms of security.
Telnet, the older protocol of the two, offers a simple and straightforward way of connecting to remote devices. However, it is less secure. Telnet transmits data, including passwords, in plain text, making it vulnerable to interception. This lack of encryption makes it a risky choice for transferring sensitive information. That is why it is best to avoid it for confidential communications.
On the other hand, SSH (Secure Shell) is the modern and more secure option for remote access. It encrypts data in transit, which helps ensure confidentiality and integrity. SSH employs robust authentication methods, making it a more reliable and safe choice for remote administration and file transfers. It is widely adopted in the IT world, which is a sure sign of its trustworthiness.
In summary, while Telnet is still a possible option for non-sensitive connections, SSH appears as the most suitable choice when security is a top priority. The right choice between them depends on the nature of the data you’re handling and the level of security required.
Conclusion
Now you know what Secure Shell actually is and how it works. For sure, it is one of the most amazing inventions regarding establishing secure connections.