DDoS Attacks are widespread threats on the Internet. With the continually increasing numbers of connected devices and new innovative ways of hacking them, we can’t just stay and wait to get affected. We should smartly implement a robust DNS infrastructure and choose a trusted DNS provider, that offers DDoS attack protection, to be safe and to evade the downtime of our services.
But to be protected, we must know the danger!
Table of Contents
What is a DDoS attack?
DDoS attack stands for Distributed Denial-of-Service attack and represents a cyber-attack that aims to disrupt normal traffic and make the target (website, server, network) unavailable for regular users. There are few different types, but in general, a DDoS attack is an attempt to overwhelm the target (a computer, few connected computers or a whole DNS network) with high traffic from multiple sources.
The cybercriminals can generate this strong wave of traffic by:
- Using a network of pre-infected devices (computers, mobiles, IoT devices, etc.) called a botnet
- Amplify attack that uses other servers to resend the traffic to a target after significantly increasing the size of the packets
- Occupy the existing connection and not allow new ones
- Exploit the vulnerabilities of a protocol, such as the UDP or another.
There are many DDoS threats, this is why you want to a DDoS defense too. DDoS attack protection could keep your business safe and notify you of problems.
Ready for ultra-fast DNS service? Click to register and see the difference!Experience Industry-Leading DNS Speed with ClouDNS!
How does it work?
There are different types of DDoS attacks (volume-based attacks, protocol-based attacks, and application-layer attacks), but in general, they all have the same stages:
- Pre-production of the attack. At this moment, the cybercriminals will create a network of botnets (infected devices) that later they will use for attacks. For example, hackers can bypass the security of IoT devices, or they can send phishing emails to users, and when the users open the emails, they can get infected with malicious code.
- Launching of the attack. Now it is time to use the botnet. Time for choosing a victim and sending the traffic towards the targeted server. There are different reasons for the attacks, but the goal is to saturate the target with traffic and take it out of service.
- The success of the attack. After a while, if the target does not have DDoS attack protection, or it is not strong enough, eventually it won’t be able to function correctly. There is a limit to how many active connections a server can have, even if it is very powerful. It will start to deny service and stop working. Normal users will not be able to use the server until the traffic drops again and the server can begin responding to normal queries.
- Final result. The bad actors could have achieved different goals, and now they get their reward. It could be money or just satisfaction with the success of the attack.
Signs of DDoS attacks
DDoS attacks are extremely harmful and could lead to large reputational and financial losses. That is why it is crucial to be mindful and observe for any early signs of an appearing attack. There are specific characteristics of each DDoS attack type, but in general, what you can expect during an attack is:
- Strange traffic, coming from one IP address or various but similar IP addresses (same range of addresses).
- Traffic coming from devices with a similar profile (the type of devices, OS, etc.) and same patterns.
- Out-of-ordinary traffic spikes like a huge spike, in the middle of the night without any sense or repeatable traffic, with a particular interval.
- Traffic only to a single page, and no further exploration of your website.
DDoS vs. DoS
Let’s first briefly define a Denial of Service (DoS) attack. In this type of online attack, a source is maliciously infected in order to send big amounts of traffic to a target. The purpose is to saturate the system, to make it crash by exhausting its technical resources (CPU, RAM, etc.), or by exploiting a specific vulnerability and injecting a proper, harmful input. Then the service for users will be denied.
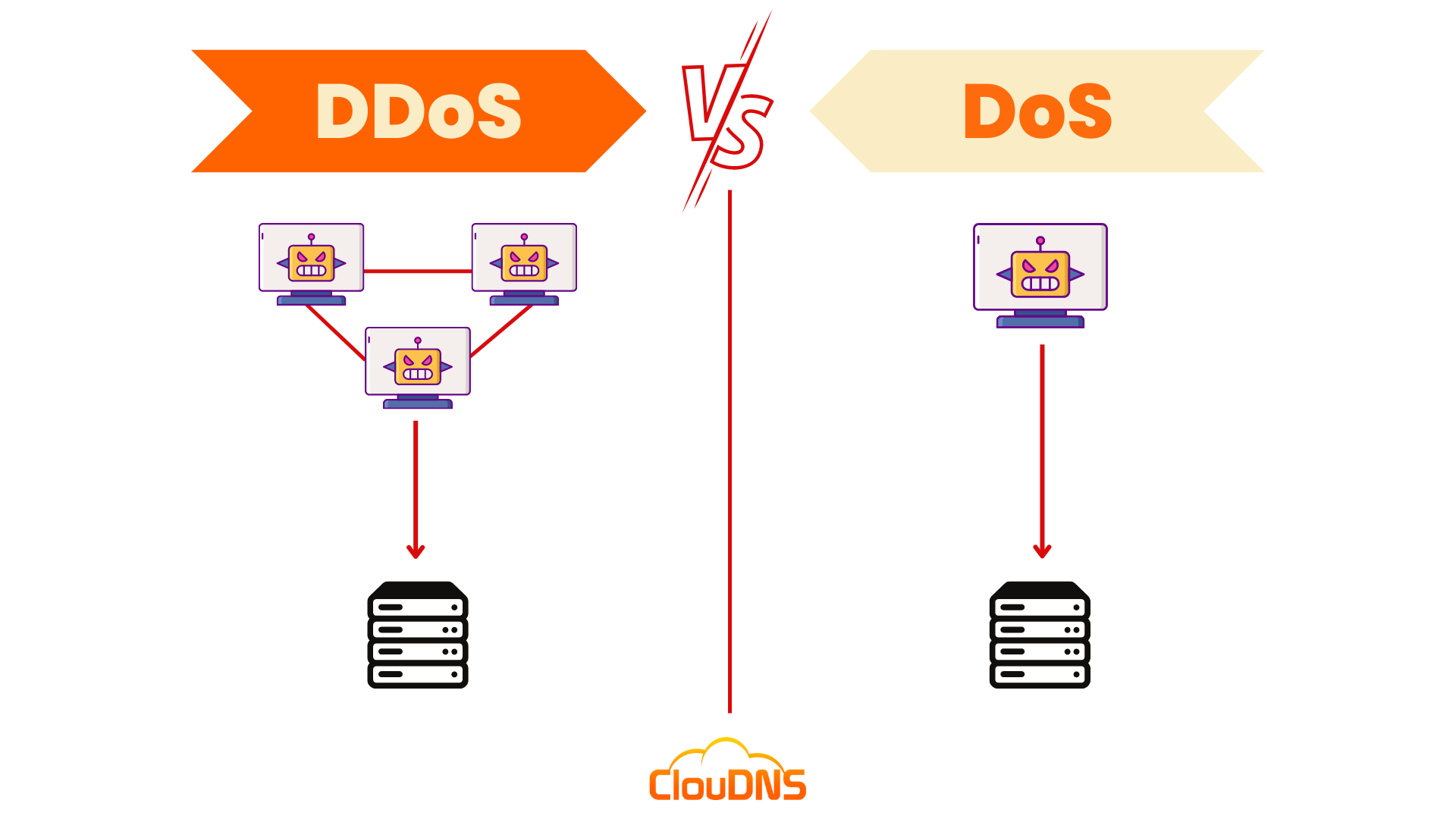
Now, let’s jump to the differences between DDoS vs. DoS attacks:
- Sources for attacking. In DoS attacks, the perpetrator only needs one Internet-connected device (source) to flood its victim with lots of forged requests or exploit a specific vulnerability within its software. DDoS attacks are executed from multiple sources, thousands, even millions of devices connected to the Internet.
- Way of execution. Generally, DoS weapons are apps like Low Orbit Ion Cannon or homemade codes. DDoS perpetrators use botnet armies, massive groups of malware-infected devices like PCs, routers, mobiles, Internet of Things (IoT) connected to the Internet. The traffic a DDoS attack can produce is heavy, much bigger than a DoS attack can.
- Damage scope. Both attacks can be very aggressive. But still, modern technology makes it easier to defend and even track the malicious source of a DoS attack, increasing the chances of identifying it and defeating it. It becomes a one-to-one fight (DoS). During a DDoS attack, you are fighting against multiple devices, possibly located in different countries or continents. You would have to track and stop all of them simultaneously. This is more like a war, and it definitely will demand so much more time and resources for the victim to defend and try stopping the attack. Thus, the damage scope of a DDoS is wider than the DoS one.
DDoS attacks Protection
There is a solution that can stop most of the DDoS attacks, even a strong attack involving heavy traffic, called DDoS Protection. It is an additional service to a regular managed DNS plan.
To successfully mitigate a DDoS attack, you need to have the following 3 elements:
- Active monitoring. You need a Monitoring solution system that checks for signs of attacks like increased traffic, suspicious traffic from particular IP addresses, and strange patterns of requests.
- Reactive service. One thing is to see the danger. Another is to take action. Good DDoS protection service must have auto triggers that will take action. This may include load balancing, traffic filtering, and an alarm system.
- Traffic load balancing. When we talk about heavy traffic, you need to direct the traffic to more servers. That way, you will balance the hit on one and disperse it to more. The more DNS servers your plan includes, the better possibility you have to resist the DDoS attack.
You need to have an intelligent DDoS attack protection service that can distinguish between heavy traffic because of your excellent promotion or real danger. You don’t want to block your real users at any moment.
Discover Web monitoring from CloUDNS
What is the motivation of DDoS attackers?
Cybercriminals can have multiple reasons to use a DDoS attack, and the most common are:
- Extortion. The attacks can send waves of traffic towards the target and disturb the functionality of its services, causing technical problems, downtime, and miss of sales, demanding money for stopping the DDoS attack.
- DDoS-for-hire to attack the competition. On the Dark Web, people can hire hackers for DDoS attacks. Some people pay for such an attack to be directed towards their competitors. It is especially popular during important sales moments like Christmas, Black Friday, Cyber Monday, or Easter promotions. If the competitor is down, it won’t receive visitors on its site, and they will go to another place. The one who paid the attack hopes a part of these visitors directs to its site.
- Cyberwarfare. The governments of some countries use DDoS attacks to target the opposition’s news sites, their communication, or other crucial services. The goal is to control the narrative and not allow free speech in their country. These attacks could be especially strong because countries have a lot of money for sponsoring them.
- Gamers’ conflicts. You could be surprised, but the gaming industry has already reached almost 200 billion dollars in revenues per year, so the stakes are high. Rival gamers use DDoS attacks to bother their competitors and try to lower their scores. Sometimes, they use DDoS to stop a competition game they are losing and demand a re-match.
- Hacktivism. Hackers also have an opinion. They might have a problem with the government, with a particular organization or event. Modern activism has many new ways to protest and express a point that includes cyberattacks.
Types of DDoS attacks
Over time, cyber criminals managed to create multiple technical approaches for taking out their victims through DDoS. Each of the techniques falls into one of the three general types of DDoS attacks, which are the following:
Volume-Based or Volumetric Attacks
These are the most classic type of DDoS attacks. They use different methods for generating massive volumes of traffic to overwhelm the capacity of the victim’s resources. As a result, servers are overwhelmed with requests, networks are overwhelmed with traffic, and databases are overwhelmed with calls. Additionally, they saturate bandwidth and produce large traffic, which results in it being impossible for legitimate user traffic to flow into the targeted website.
Protocol Attacks
Protocol attacks, also known as state-exhaustion attacks, abuse protocols to overwhelm a particular resource, most commonly a server but occasionally firewalls or load balancers. They are designed in a way that allows them to consume the processing capacity of network infrastructure resources. Their target is usually Layer 3 and Layer 4 protocol communications and, more precisely, their weaknesses. These attacks are often measured in packets per second.
Application-Layer Attacks
These DDoS attacks target weaknesses in applications in order to force the application itself to fail. In contrast to other attacks that mainly concentrate on disrupting infrastructure, these attacks are initiated on Layer 7 (the Application layer) by opening connections and starting processes and transaction requests that consume limited resources, such as disk space and available memory. Yet, it can even result in overloaded CPUs or exhausted memory, which impacts the server and other applications. Layer 7 attacks are well-known that are difficult to prevent since it can be challenging to distinguish malicious traffic from regular traffic. Application DDoS attacks are usually measured in requests per second.
In real-world cases, criminals can actually use a combination of these types of DDoS in order to increase the intensity of the attack.
Popular DDoS attacks used by hackers
Let’s talk a little bit more about the most popular types of DDoS attacks initiated by cybercriminals!
Smurf Attack
The Smurf attack is performed over the ping tool (ICMP echo request). The ping tool is used to check the reachability of connected devices. When you send a ping request to the destination address, you should receive a confirmation. In this DDoS attack, the ping is sent to a device but from a masked IP. The return confirmation doesn’t go to the original source, but it is redirected to the target of the attack. All the infected devices will do the same, and they will send the traffic to the victim.
Teardrop Attack
A Teardrop attack works by sending modified, oversized data packets to the victim’s device to make them inaccessible. Frequently, perpetrators use a specific bug for destabilizing the fragmentation codes or the reassembly feature of the TCP/IP protocol. This opens the door for the teardrop attack to happen.
Reassembling the maliciously modified data packets won’t be possible. This will produce repeated attempts to complete the task. And the constant cycle of these repetitions will cause the overlapping of the packets. Finally, to increase the strain, big traffic loads will be sent to the target for a definitive crash.
Ping Of Death
The Ping Of Death (POD) attacks using a common and valid tool with malicious objectives – the Ping command. Altered or oversized data packets are sent to the target through the ping command.
Consider that a correct IPv4 data packet (IP header included) must be 65,535 bytes. This is the standard allowed by the Internet protocol (IP). Perpetrators violate it and make the target struggle while trying to reassemble altered packets repeatedly. Target’s resources like memory will be exhausted, causing different problems, crashing included.
POD became popular because attackers don’t need deep knowledge about its victim, only its IP address.
Slowloris
A highly dangerous attack executed a single computer vs. a server. A sophisticated technique that takes down a server without disrupting the rest of the network’s ports and services. Slowloris operates by sending many partial requests to the server. It keeps sending more and more HTTP headers continuously but without completing those requests. These forged requests keep many connections open to the server for a longer time than usual to overwhelm the maximum concurrent connection pool. As a result, the system will slow down, additional connections from legit users will be denied.
Zero-day DDoS attack
A Zero-day, also called a zero-minute attack, is one that takes advantage of new vulnerabilities. People are not yet aware of them. Usually, those vulnerabilities appear on new updates or patches, but they can also exist since the software is launched. The name of the attack refers to the fact it is happening before the vulnerability perpetrators used is publicly known.
This attack can have a positive purpose when software companies pay people in exchange for reporting vulnerabilities of new products before their official release. But it also points to the reality that attacks are far from disappearing.
Preparing a DDoS attack
To launch a DDoS attack, first, the criminals need to “recruit” enough connected devices that later will generate the traffic. To do so, they infect those machines with different malicious software (from emails, visiting unprotected sites and more) and create so-called botnets – hijacked devices ready to be used when it is time for the attack. There are even markets for botnets, where you can buy an attack on a website of your choice.
The Consequences of DDoS attack
Experiencing such a harmful threat is highly unpleasant and can have a huge negative impact. Some of the possible outcomes of a successful attack include:
- Operational Disruption: One of the immediate consequences of a successful DDoS attack is the disruption of normal operations. Websites become sluggish or entirely inaccessible, leading to frustrated users, decreased productivity, and financial losses. E-commerce platforms, financial institutions, and online services are especially vulnerable, as downtime translates directly into revenue loss and damage to customer trust.
- Financial Loss: DDoS attacks can cause severe financial harm. Businesses may face not only the direct costs of mitigating the attack and restoring services but also indirect costs associated with reputational damage and lost customers. The financial damage can lead to legal consequences, especially if sensitive client information is compromised during the attack.
- Reputational Damage: Trust is a delicate matter in the digital space, and a DDoS attack can destroy it instantly. When customers cannot access services or experience disruptions, they may lose confidence in the affected organization and its ability to protect their interests. Rebuilding a reputation can be a long and difficult process.
How long does a DDoS attack last?
The duration of a DDoS attack can vary significantly based on the resources available to the attackers and the defensive measures of the target. DDoS attacks can last from a few minutes to several weeks. On average, however, most DDoS attacks last for around 24 hours, though some intense attacks can go on for days or even weeks.
Short-duration attacks can be a part of a coordinated strategy where attackers test a target’s vulnerabilities with brief bursts, estimating the response and preparedness of the target’s systems. These “hit-and-run” style attacks can cause considerable disruption in a short time, particularly if they target time-sensitive operations like financial transactions or sales events.
Prolonged DDoS attacks typically aim to exhaust the target’s resources or force them to pay a ransom in exchange for stopping the attack. Long-term attacks can be devastating as they may prevent an organization from functioning entirely, leading to major operational and financial issues.
Preparedness and robust DDoS protection are essential to mitigate the effects of both short and prolonged attacks.
Which industries are being targeted and why?
Certain industries are more frequently targeted by DDoS attacks due to their high online activity, competitive nature, and dependence on continuous uptime. Here are some of the industries most affected and why they are popular targets:
- Financial Services and Banking: Financial institutions are high-value targets due to their critical role in managing and securing funds and customer data. Attackers may aim to disrupt operations, damage reputation, or extort these institutions for ransom. A successful attack on a bank can lead to significant financial loss, operational chaos, and damage to customer trust.
- E-commerce and Retail: Online retail is another major target, especially during peak shopping seasons like Black Friday and holidays. Attacks during these times can severely impact sales revenue, as website downtime directly translates to lost customers and sales.
- Government and Public Sector: Government websites, especially those related to public communication, law enforcement, and emergency services, are frequent targets. These attacks may be politically motivated, intending to disrupt public access to information. Governments are also targeted to disrupt official communication channels.
- Gaming and Entertainment: The gaming industry is particularly vulnerable, as users expect real-time access and responsiveness. Gamers often participate in competitive or time-sensitive events where even short downtimes can lead to significant frustration and financial loss for companies. DDoS attacks are frequently employed to disrupt gaming servers.
- Media and News Websites: News outlets and media websites are also prime targets. Hacktivists may use DDoS attacks to silence certain news outlets or delay the publication of specific content. Attacks on these sites can reduce public access to information, potentially affecting the narrative on important topics.
How to prevent a DDoS attack and stay safe?
The cyber-criminals can make a vast network of botnets, but it doesn’t mean you can’t be protected. ClouDNS provides you two options to stay away from DDoS troubles.
You can choose and subscribe for a DDoS protected DNS.
All plans provide unlimited Layer 3-7 DDoS Protection. Whichever you pick from them, you will be able to use 4 DDoS protected DNS servers, 50+ Anycast locations and unlimited DNS queries. For big companies, we recommend our DDoS Protection L subscription with 400 DNS zones that you can manage.
Or you can use a Secondary DNS as a backup DNS, so you always have a backup copy of your DNS records.
It adds resilience, reduce the outage periods by answering requests even if the Master is down.
Conclusion
The more extensive your DNS network is, the better. The massive traffic from the attackers can be distributed between your servers in the different locations, and it will ease the load. Don’t forget that modern DDoS attacks target different communication layers, so you will need intelligent DDoS protection to respond fast and accurately.
To be safe, always choose quality DNS service provider like ClouDNS.






