Cybercriminals often use Botnet for their malicious purposes. That way, they build their army of devices and execute massive attacks. So let’s dive deep and explain more about Botnet and how the Botnet attack works.
Table of Contents
Botnet – What does it mean?
A Botnet is a network of different devices, like computers, smartphones, tablets, and IoT, which are infected with malware and controlled by a cyber-criminal, also known as a bot herder. Each individual device within the botnet network is also known as a bot or zombie.
These hijacked devices are utilized to carry out different scams and cyberattacks, like sending spam emails, distributing malware, and preparing DDoS attacks. The assembly of a botnet is usually the infiltration step of a multi-layer scheme. Botnets employ the devices of regular users for scams and disruptions without requiring the permission of the owner.
You are probably wondering what the botnet attack actually is and how it works. So, let’s expand the topic and clarify for what purposes they are used!
What are botnets used for?
There are different reasons why attackers use botnets. However, the most popular intentions are related to stealing data and money. Here are some of the most common usages of the networks of hijacked devices:
Fraudulent or money stealing
Cybercriminals can perform attacks that involve a botnet network for stealing money directly or indirectly. Some of the popular methods to achieve that are phishing emails or making a fake website that looks exactly like the original bank website, for example. Then, they are able to translate the payment or transaction details and utilize them to steal money.
Data theft
The data of the users is highly valued in the market. Cybercriminals are well aware of that. Therefore, they use botnets for stealing individual personal information, or even more, they break into the database of a precise company. The next step for them is to sell the user information to third parties and make a profit from it. These botnets could stay inactive and only steal personal details.
Perform spamming and phishing frauds
By implementing botnets, attackers can execute large email spamming and phishing scams. That is because they can spread malicious emails to numerous targets easily. Moreover, there are spam botnets that are precisely designed for such tasks.
However, the intentions are always the same, meaning stealing money or information, even if the methods differ. Yet, there are a specific group of cybercriminals who use botnets only because they can. They only aim to show their abilities and demonstrate their superiority to the rest of the world. There are different examples of security breaches where the attackers steal personal details and reveal them on the dark web for free.
Experience Industry-Leading DNS Speed with ClouDNS!
Ready for ultra-fast DNS service? Click to register and see the difference!
Botnet attack – explained in detail
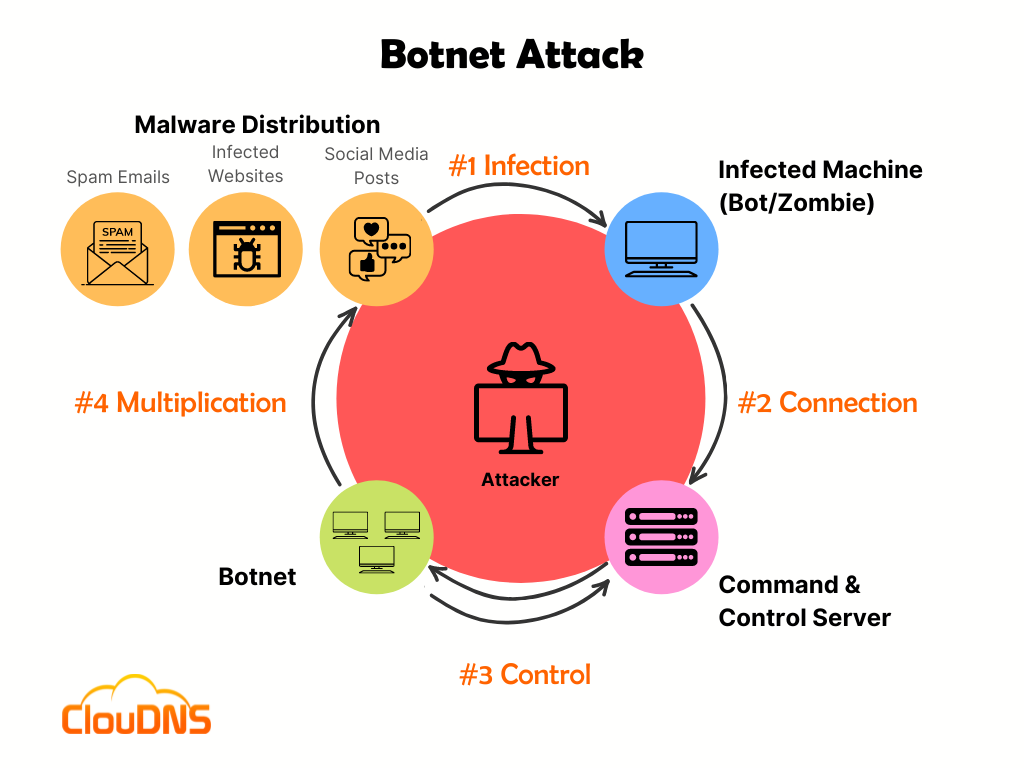
We talk about a Botnet attack when cybercriminals inject malware into the network to control them as a collective used for initiating cyberattacks. Otherwise, botnets themselves are simply a network of devices.
The scale of a Botnet attack could be pretty large, and any device could fall victim to it. So, cybercriminals use additional machinery or devices to support and improve the mastership of a botnet.
Bot herder is needed to guide and control the group of hijacked devices in the network. The attacker uses it via remote commands to guide the devices and make them complete specific actions.
Bot or zombie computer is an infected device (system) used to create a botnet. The bots are guided by the bot herder’s command, and they behave by its instructions.
Let’s break down the construction process of a Botnet attack. Here are 3 main steps you should know:
Step 1: Prep and Expose
The cybercriminal discovers a vulnerability to introduce into the user’s device. The process of searching for a vulnerability involves the website, human behavior, and application. That way, the attacker prepares a set-up to drown the victim to get exposed to malware without notice. Typically, the vulnerabilities are found in websites and software, and the malware is delivered through emails or messages.
Step 2: Infecting the user
The attacker activates the malware, and the user’s device is infected and has compromised security. Typically, for that purpose, cybercriminals use the social engineering method or the Trojan virus. Another more aggressive approach includes deploying drive-by-download strategies to infect the device. However, with all of these methods, cybercriminals aim to weaken the target with botnet malware.
Step 3: Taking control over the targeted devices
The last step is taking control of each infected device. All of them are systematized, and the attacker involves a method for managing them remotely. Numerous devices are under control through a massive zombie network. After completing this step, the cybercriminal gains admin-like access to the targeted devices. Moreover, it has the ability to read and change the stored information, capture it, share it, or watch all of the activities on the device.
Most popular Botnet attack types
Botnets are attacks by themselves also, but they are a perfect instrument for performing secondary frauds and cybercrimes on a giant scale. Here are the most popular Botnet attack types:
DDoS attack
DDoS attacks aim to overwhelm a target server, network, or device with massive traffic. The zombie devices (bots) send large amounts of requests aiming to crash or at least slow down the target significantly.
That is one of the most popular forms of using botnets for criminal purposes. Additionally, it is commonly the one that is the most dangerous. The negative effects of DDoS attacks are often long-term and severe. That includes not only financial losses but also reputational damages for the target organization.
That is critical for everyone that has a functional website and especially for businesses that operate and offer their services online. So for sure, proper DDoS protection is a must! Unfortunately, it is already too late for you to plan your response when a DDoS attack appears. Therefore, protection and mitigation should be planned.
Phishing
Botnet attacks are commonly built by phishing tactics. That way, they infect more devices and extend the size of the botnet.
Additionally, phishing and other methods of social engineering attacks include a botnet that sends emails, posts comments or sends messages on social media acting like people or businesses that the victim trusts, commonly used to steal your banking details.
Precisely phishing is hard to defend against because humans easily fall victim to them.
Brute Force attack
Another popular way that bot headers use botnets is to complete different Account Takeover (ATO) attacks, mostly Brute Force attacks (credential cracking).
For a Brute Force attack, the zombie devices are instructed to test the various options of a user password and “crack” it. For instance, if there is a PIN with 4 digits, bot device 1 is going to test “0000”, the second bot device is going to test “0001”, etc. That continues until one of them guesses the correct PIN.
Defending against this botnet attack is also very challenging. It is effective in exploiting weak user credentials.
Which devices can become targets of a Botnet?
Devices infected with malware, also known as “bots” or “zombies,” can be remotely controlled by attackers. Almost any device with an internet connection can potentially become a target for a botnet if it has vulnerabilities that can be exploited. Here are some common types of devices that can be targeted:
- Personal Computers: Desktops and laptops running various operating systems, including Windows, macOS, and Linux, can be targeted by botnets if they have security vulnerabilities. Malware can infect these devices through malicious downloads, email attachments, or drive-by downloads.
- Servers: Web servers, email servers, and other types of servers are attractive targets for botnets because they often have high-speed internet connections and large resources. Compromised servers can be used to host malicious content, launch DDoS attacks, or distribute malware.
- Mobile Devices: Smartphones and tablets are also exposed to botnet infections. Malicious apps, compromised app stores, and phishing attacks can be used to target these devices. Both Android and iOS can be affected by botnet-related threats.
- IoT Devices: Internet of Things devices, such as smart cameras, smart thermostats, routers, and smart appliances, are targeted by botnets. They are often less protected and may have default or weak passwords, making them easy targets for exploitation.
- Network Equipment: Routers, switches, and other devices can be compromised by botnets. Once infected, these devices can be used to control network traffic, redirect users to malicious websites, or participate in DDoS attacks.
Signs your device could be part of a Botnet
Here are the most common signals that your device could be part of a Botnet:
- Unusual Sluggishness: If your device suddenly becomes slow or unresponsive, it may be because a botnet is using its resources.
- Excessive Data Usage: A sudden spike in data usage without an apparent reason could indicate your device is participating in botnet activities.
- Unwanted Pop-ups: Frequent pop-up ads or redirects to suspicious websites may signal that your device is under the control of a botmaster.
- High CPU Usage: Constantly high CPU usage, even when you’re not running intensive applications, can indicate malicious activity.
- Outbound Spam Emails: If your email contacts receive spam from your account without your knowledge, your device may send spam as part of a phishing attack.
- Disabled Security Software: Malware in a botnet often tries to disable antivirus and firewall protection to avoid detection.
- Unexplained Software Installs: Unauthorized software installations or changes to your device’s settings can be a sign that attackers may have control over it.
- Strange Network Activity: Monitor your network traffic for unusual patterns, such as frequent connections to unfamiliar IP addresses or domains.
How to protect yourself?
Here are some things you can do to protect yourself from botnet malware.
- Strong passwords. Make sure all of your smart devices have complex long passwords. That will keep them safer compared to a short and weak password, like “123456”.
- Update your OS. You should update your software. That way, you are receiving all of the security patches that can deal with familiar vulnerabilities.
- Change admin settings and passwords across all of your devices. Make sure to check all potential privacy and security options. That includes everything that connects device-to-device or to the Internet. If you skip changing to custom login credentials and private connectivity, cybercriminals will be capable of breaching and infecting all of your devices.
- Avoid opening suspicious email attachments. Before you download a file, make sure to verify the sender’s email address.
- Avoid clicking on links in messages. Different texts, emails, or social media messages could include malware. Moreover, by doing so, you can avoid drive-by downloads and DNS cache poisoning.
- Reliable antivirus software. It is going to help you improve your security and keep yourself protected from Trojans and other threats.
Impact of Botnets on Businesses
Botnets are a growing threat to businesses of all sizes, exploiting weak spots in networks to carry out malicious activities. Here’s a breakdown of how they can impact your business:
- Financial Losses
Botnets can cause serious financial damage. They might steal sensitive data directly, demand ransoms after launching ransomware attacks, or disrupt your services, leading to lost revenue. For example, a Distributed Denial of Service (DDoS) attack could take down your website, resulting in significant downtime and a drop in productivity.
- Damage to Your Reputation
The impact of a botnet attack goes beyond immediate financial losses. It can also severely damage your company’s reputation. Customers and partners may lose trust in a business’s ability to protect confidential information, resulting in long-term loss of clientele. There could also be legal consequences if your company fails to comply with data protection laws. Recovering from such an attack often requires significant investment in cybersecurity measures, system restorations, and efforts to rebuild public trust.
- Increased Operational Costs
Botnet infections can also lead to the unauthorized use of company resources, increasing operational costs and exposing internal systems to even more security risks. Small and medium-sized businesses are especially vulnerable, as they might not have the necessary infrastructure or expertise needed to effectively defend against these threats.
To reduce the risk of botnet attacks, it’s essential to adopt proactive security measures and include regular employee training, robust incident response plans, and a strong focus on cybersecurity. By taking these steps, you can help protect your business from the negative effects of these attacks.
Some famous Botnet attacks
Mirai – 2016
The massive Mirai botnet attack was initiated through a DDoS attack, and it made the Internet unavailable in the U.S. It was the first major botnet that infected insecure IoT devices. At the peak of the attack, it got to over 600,000 infected devices.
3ve – 2018
3ve, pronounced Eve, started as a small botnet. Yet, the number of infected devices reached a tremendous 1.7 million. The botnet managed to falsify billions of ad views. As a result, businesses paid millions for ads that no real human, a regular internet user, ever saw.
Why Are Botnets So Hard to Stop?
Botnets are difficult to stop because they are made up of thousands, sometimes millions, of infected devices spread all over the world. These devices don’t belong to the attacker. They belong to regular people who often have no idea their computers, phones, or smart devices are being used in a botnet.
Even if a cybersecurity team shuts down one server that controls the botnet, the attacker can simply switch to another. Some botnets use advanced techniques like encryption or peer-to-peer communication to hide how they operate. On top of that, cybercriminals often stay anonymous by using tools that hide their location, making it harder for authorities to catch them.
Stopping a botnet usually requires cooperation between internet service providers, cybersecurity experts, and law enforcement across different countries, which can take time. That’s why prevention and early detection are so important.
Conclusion
Botnet and Botnet attacks are cyber threats that should not be neglected! It is important to keep yourself or your organization safe from such malicious attempts. Otherwise, they could lead to large financial and reputational damages!