Have you ever heard of rDNS? It may not be as well-known as its opposite, forward DNS, but in today’s digital world, rDNS plays a critical role in preventing spam and network troubleshooting. In this article, we’ll explain rDNS in more detail and discuss its importance and various use cases. Let’s get started!
Table of Contents
What is rDNS?
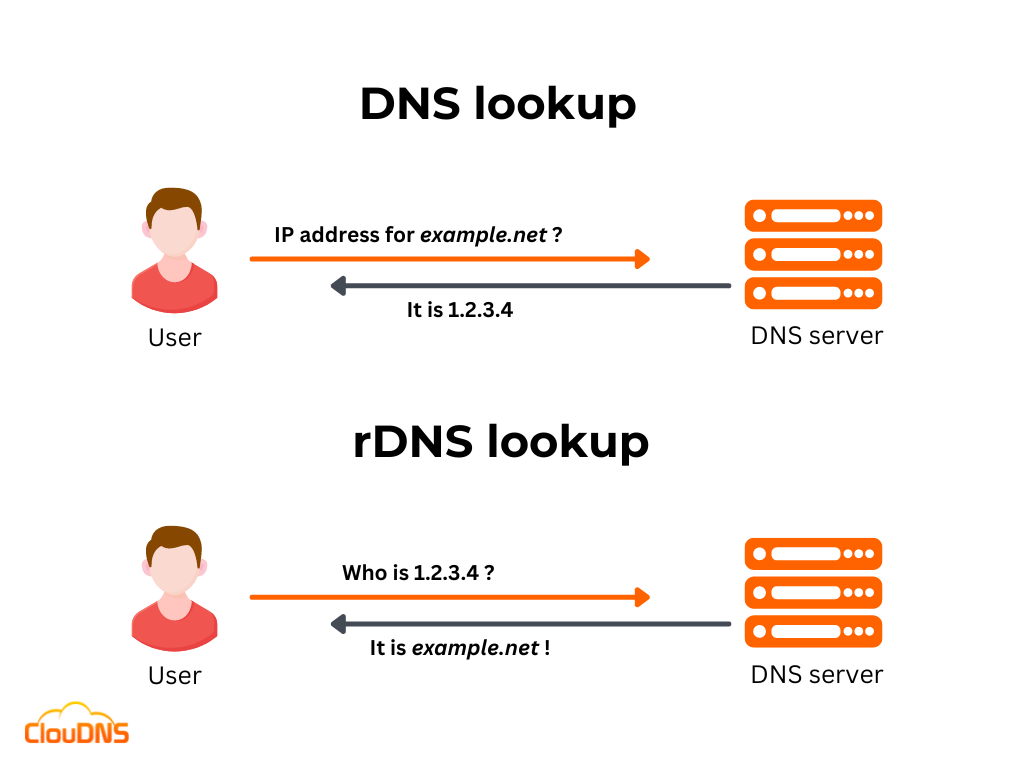
You probably already know what a forward DNS is. It links the associated hostname/domain to the IP address. Now think from the opposite direction. rDNS, also known as Reverse DNS, is doing the mirror action, using the IP address to find the hostname/domain name. You might be surprised that this is actually needed, but it has significant application. It is very useful for email verifications B2B and troubleshooting.
Imagine this situation, you don’t have a reverse DNS set up, but you are sending a very important email to another company. They have a mail server with Anti-Spam protection. It will check if you have rDNS and if you are missing it, your message will go directly to the spam bin. This protection reduces the phishing significantly by putting straight into the spam, all emails that have IPs that don’t correspond to IPs of the domains they say they come from.
All devices connected to the internet have their IP addresses. This makes it easy to do a reverse DNS lookup and see who it is on the other side. For this purpose, you will need a PTR record.
Check out Reverse DNS service by ClouDNS!
Why is rDNS important?
There are several reasons why rDNS is crucial. Some of them are the following:
- Email Authentication: rDNS helps authenticate email servers and prevent spam. A large number of email servers will only accept incoming emails from hosts with a valid PTR record. That way, they avoid spam and phishing emails from spoofed IP addresses.
- Network Troubleshooting: rDNS can be used to help troubleshoot network issues. If a network administrator is trying to diagnose a problem with a specific IP address, they can use rDNS to determine which hostname is associated with it. This can help them identify the device or service causing the problem.
- Protection: Some security systems use rDNS to identify and block malicious traffic. For example, some intrusion detection and prevention systems will use rDNS to recognize and stop traffic coming from known malicious IP addresses.
- Access Control: In some cases, rDNS can be used to control access to a network or specific services. For example, some firewalls and VPNs use rDNS to allow or deny access to particular hosts or services based on their hostname.
Ready for ultra-fast DNS service? Click to register and see the difference!Experience Industry-Leading DNS Speed with ClouDNS!
How does rDNS work?
The main goal of rDNS is to map an IP address to a hostname. In order to achieve that, it works by performing a reverse lookup of an IP address to find the associated domain name.
The process of rDNS starts with a query to a DNS server, asking for the hostname associated with a specific IP address. The DNS server then looks up the available IP address in its records, and if it finds a match, it returns the associated hostname.
Reversing the forward DNS process and resolving an IP address to a domain name requires a Reverse DNS zone and a PTR record. So, let’s explain a little bit more about them!
PTR record
The PTR record is also called a Pointer record, and its primary purpose is to link the IP address to its corresponding hostname/domain name. It is important to note that you should have an A or AAAA record for each PTR record you create. The explanation behind this practice is pretty simple. An A record or AAAA record maps a hostname/domain name to its IP address, and PTR goes exactly in the opposite direction. That is why it is essential to ensure you configure your DNS records accurately without any mistakes. Otherwise, there is a possibility for your emails to land directly into the spam folder of your recipients.
Reverse DNS zone
Using rDNS requires creating a special type of DNS zone called a Reverse DNS zone. That is the only place where PTR records are able to exist and function correctly. Reverse DNS can work both with IPv4 addresses and IPv6 addresses, yet they should be written in reverse. That is because there is a specific root domain in-addr.arpa that uses the IP addresses in reverse order. So, for example, the IP address 111.123.101.1 becomes 1.101.123.111.in-addr.arpa.
How to start using rDNS?
The first step is to create a Reverse DNS zone; you can do that from the Control Panel, add a new zone and click on the Master Reverse DNS zone.
Watch the video to find out how to add Master Reverse DNS zone
This zone is directly related to the size of your IP network. For example in IPv4/24 network, you will have 255 IP addresses. In the network 192.168.1.0/24, all the available IPs will be from 192.168.1.1 to 192.168.1.255, and the Reverse DNS zone will have this format 1.168.192.in-addr.arpa
Now in this Reverse zone, we can add PTR records that match each IP from the network. You just add a new record; this will be for the first IP 192.168.1.1
Type: PTR
Host: 1
Points to: hostname1.example.com
The PTR records will look like this in the Control Panel:
| Host: | Type: | Points to: | TTL |
| 1.1.168.192.in-addr.arpa | PTR | hostname1.example.com | 1 Hour |
Then, make sure that there is a matching A record. Each PTR must have one.
Find more information about PTR records and how to create them!
The last step is to change the name servers of your Reverse zone at your IP provider or ask them to do it. A configured NS records at the IP provider must point to the name servers listed in your Control Panel.
What in-addr.arpa is?
in-addr.arpa is a critical component in the architecture of Reverse DNS (rDNS), playing a pivotal role in how rDNS functions. This special domain is used specifically for mapping IP addresses to domain names, which is the essence of rDNS. Here’s a concise overview:
- Purpose: Used for IPv4 reverse DNS lookups, in-addr.arpa facilitates the conversion of IP addresses into a format suitable for DNS queries. This process is vital for various network services, especially email authentication.
- How it works: An IP address like 192.0.2.1 reverses to “1.2.0.192.in-addr.arpa“. A DNS query for this domain retrieves the associated domain name via a PTR record, crucial for verifying communication sources.
- IPv6 addresses: For IPv6, a similar domain called “ip6.arpa” is used, reflecting the distinct structure of these addresses.
- Management: Managed by IANA, in-addr.arpa’s namespace is partly delegated to ISPs for localized reverse DNS record management.
In essence, in-addr.arpa underpins rDNS, crucial for network integrity and cybersecurity efforts.
rDNS lookup – How to do it?
Now that we have explained the basics of rDNS, it’s time to show you how to perform an rDNS lookup. Besides, the process is simple, and you don’t need to have a background in IT to complete it.
- Windows
If you are a Windows user, you can perform rDNS lookup with the NSlookup command. First, open the Command Prompt by pressing the Windows key + R, then typing “cmd” and pressing Enter. Type the following command:
$ nslookup 1.2.3.4
- macOS and Linux
If you are a macOS or Linux user, you can complete the rDNS lookup with the Dig command or the Host command. Open the Terminal application and write the following:
$ dig -x 1.2.3.4
or
$ host -t PTR 1.2.3.4
*Please, make sure to replace “1.2.3.4” with the IP address (IPv4 or IPv6) you wish to check.
It’s important to note that in some cases, the rDNS lookup may not return any results if the IP address does not have a PTR record associated with it. Besides, in other cases, the response may show “NXDOMAIN” or “NXRRset”. Also, some firewalls or security systems may block reverse DNS queries.
Comparing rDNS and Forward DNS
Understanding the differences and interactions between Reverse DNS (rDNS) and Forward DNS is crucial in grasping internet infrastructure’s full scope.
Forward DNS is the process that converts human-readable domain names (like www.example.com) into IP addresses (like 192.168.1.1). This conversion is essential for internet navigation, allowing users to access websites without memorizing complex numeric addresses.
On the other hand, Reverse DNS (rDNS) works in the opposite direction. It takes an IP address and returns the corresponding domain name. This process is particularly important in scenarios where knowing the source of a network request is crucial. For example, when an email server receives a message, it might use rDNS to verify that the IP address of the sender matches the domain name claimed in the email. This verification helps in filtering out spam or spoofed emails.
The interaction between these two systems is symbiotic. While forward DNS is primarily used for routing internet traffic to the correct destinations, rDNS plays a key role in authentication and security. Together, they form a comprehensive system for both reaching and validating internet entities.
Does rDNS Improve Email Deliverability?
Yes, Reverse DNS significantly impacts email deliverability. Many mail servers use rDNS to verify the sender’s legitimacy. When an email is received, the recipient’s server performs an rDNS lookup on the sending IP to check if it has a valid PTR record pointing to a legitimate domain. If no rDNS entry exists, the email is often marked as spam or immediately rejected.
Major email service providers like Gmail, Yahoo, Outlook, and corporate mail systems consider rDNS validation an essential anti-spam measure. It helps prevent spoofing and phishing attacks by ensuring that the sender’s IP address aligns with its claimed domain.
For businesses, configuring Reverse DNS correctly is crucial for maintaining a good email reputation. Combined with SPF (Sender Policy Framework), DKIM (DomainKeys Identified Mail), and DMARC (Domain-based Message Authentication, Reporting, and Conformance), rDNS enhances email authentication, reducing the risk of emails being flagged as suspicious.
To maximize email deliverability, it is best to ensure that the outgoing mail servers have properly configured PTR records that match their forward DNS A records. This simple yet effective practice helps emails reach inboxes instead of spam folders, improving communication reliability and brand credibility.
Conclusion
rDNS is essential for email authentication, network security, and troubleshooting network issues. It performs a reverse lookup of an IP address to find the associated hostname. To achieve that, creating a Reverse DNS zone and adding PTR records is required. Thanks to this amazing technology, the Internet is a more secure place by identifying the authenticity of the source of the email, and it is beneficial for network troubleshooting.
30-day Free Trial for Premium Anycast DNS hosting