Why do we need Managed DNS?
Managed DNS is a game-changer in today’s fast-paced digital world, where the Domain Name...
How to transfer your domain name?
Domain transfer is a straightforward procedure. People do it for different reasons: some are not happy with their current domain...
What is Ping command and how to use it?
What is Ping command? Ping is a very universal command between all the operating systems. You can use it to test if you can reach your...
The Crucial Role of SSL Certificate Monitoring in Ensuring Cybersecurity
SSL certificate monitoring is like a guardian that keeps our online interactions safe and secure....
AWS vs Azure vs Google. The battle for the cloud crown
AWS vs Azure vs Google, the three biggest cloud providers in the world. They all have a vast network of servers all over the world and many...
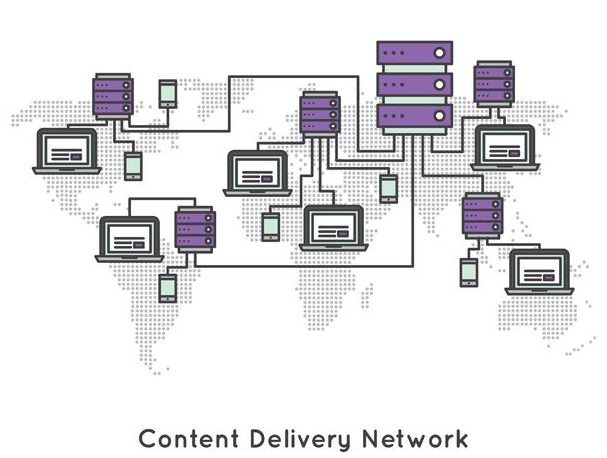
What is CDN (Content Delivery Network)?
Everybody uses CDN (Content Delivery Network). YouTube, Amazon, Netflix and many others are applying it on a massive world scale so you can...
QUIC Protocol Explained: What It Is and How It Works?
The internet is constantly evolving to deliver faster, more secure, and more reliable connections....
What is a Primary DNS server and how does it work?
We have already talked about what is DNS and what is a Secondary DNS, this time we will focus on the Primary DNS server. There is a DNS...
DDoS attacks and how to protect ourselves
DDoS Attacks are widespread threats on the Internet. With the continually increasing numbers of connected devices and new innovative ways...