UDP (User Datagram Protocol) explained in details
UDP (User Datagram Protocol) is one of the well-known protocols in network communications. Thanks...
TCPdump for Beginners: What It Is, How to Install, and Key Commands
TCPdump is a powerful command-line tool for analyzing network traffic in real-time, making it indispensable for network administrators and...
QUIC Protocol Explained: What It Is and How It Works?
The internet is constantly evolving to deliver faster, more secure, and more reliable connections. From browsing websites to streaming...
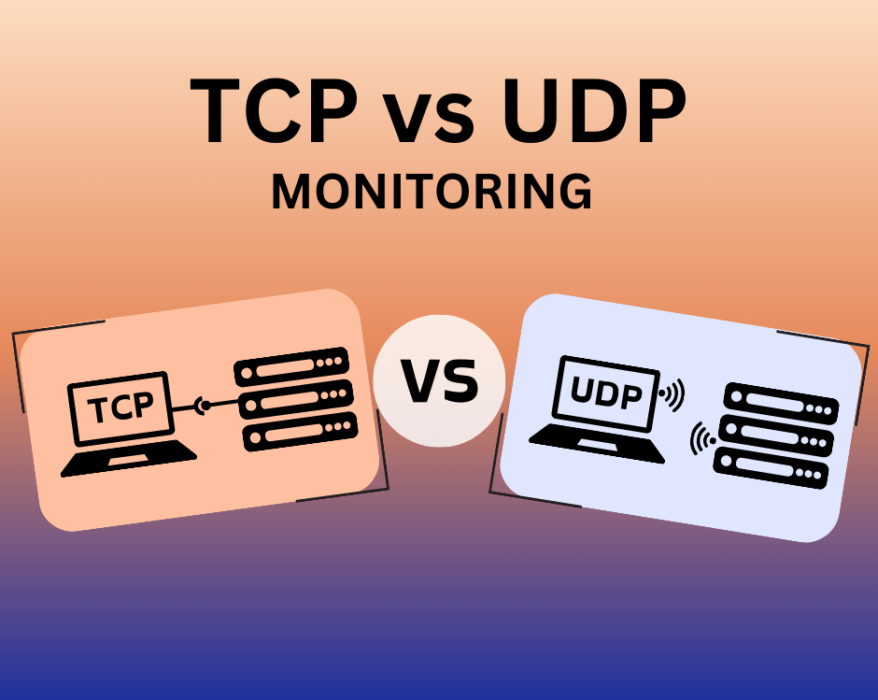
Comprehensive Guide on TCP Monitoring vs. UDP Monitoring
Why does the battle between TCP monitoring vs UDP monitoring matter in the world of network...
Understanding the Basics of SNMP (Simple Network Management Protocol)
Do you need a reliable system for monitoring and managing your network resources? Consider using SNMP! With its real-time insights and deep...
What is SNMP Vulnerability? How to stay protected?
SNMP Vulnerability is a hidden risk lurking in many network infrastructures. The Simple Network Management Protocol (SNMP) is a powerful...
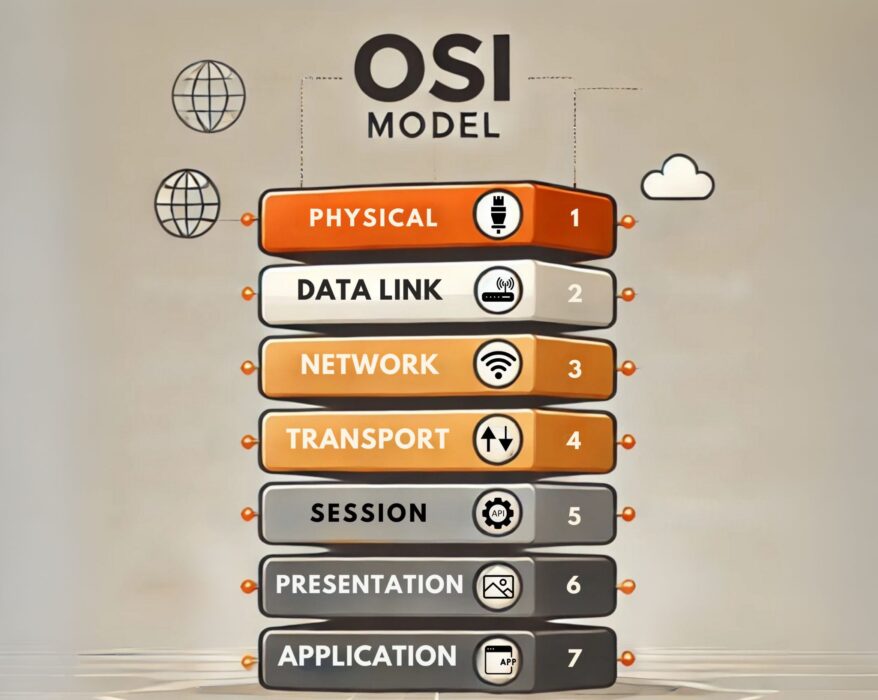
How do OSI Model layers work in computer networking?
In the vast realm of networking, the Open Systems Interconnection (OSI) Model stands as one of the...
TCP (Transmission Control Protocol) – What is it, and how does it work?
Imagine sending a message across the world and trusting it will arrive perfectly intact. That’s the magic of TCP, or Transmission Control...
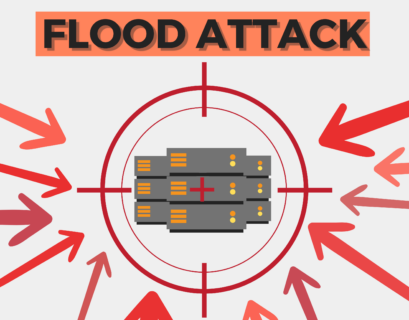
Flood Attack: Prevention and Protection
In today’s digital age, security breaches and cyberattacks have become increasingly common. One such form of attack is the...
What is ICMP (Internet Control Message Protocol)?
The ICMP (Internet Control Message Protocol) is a network layer protocol and also a supporting...