What is TLD?
The TLD is one of the fundamental things you will have to consider when choosing a domain name once...
What is Load Balancing?
Only an incredible technique like Load balancing can help you improve your performance, optimize your website, provide redundancy, and...
How to choose the best DNS for my business?
Choosing the best DNS for your business involves guaranteeing that your online presence will be handled in the most convenient way! Make...
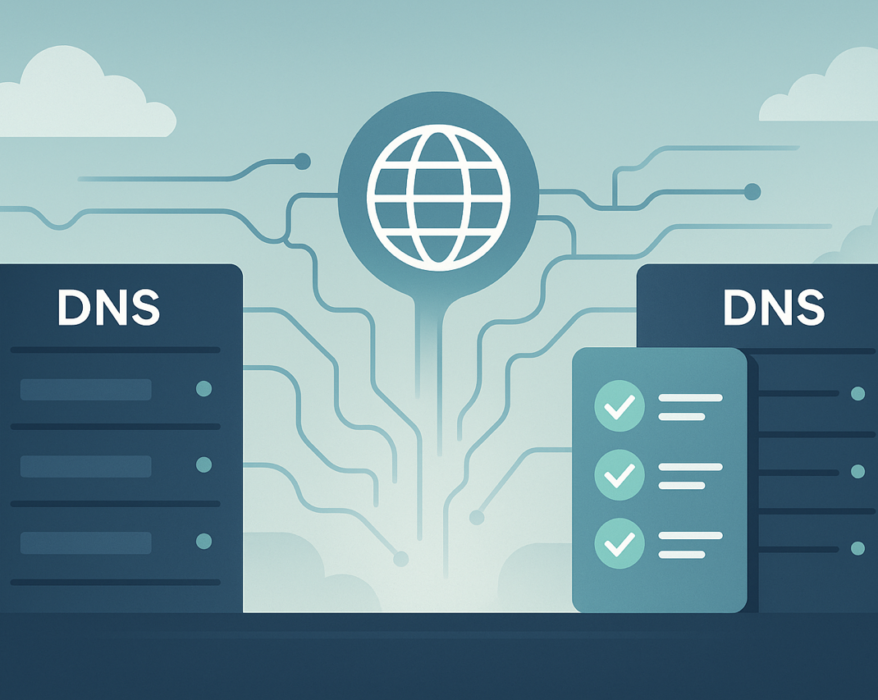
Checklist for Changing Your DNS Provider Without Downtime
Changing your DNS provider can sometimes offer significant benefits, including faster DNS...
Top 5 DNS Migration Mistakes You Must Avoid
DNS migration mistakes are more common and more costly than most people realize. Migration is one of those tasks that seem simple until...
What is Enterprise DNS?
The Enterprise DNS is a high-level class of DNS service. Its purpose is to serve large companies. It can handle a considerable amount of...
Can we use free DNS? Free DNS vs. Premium
Choosing the right DNS service is more important than many website owners realize. Whether...
DNS cache explained
The DNS is a great technology that allows us to use the internet the way we currently know it. It resolves domain names to their IP...
DNS and SEO: How does DNS service affect SEO?
At first glance, you might think that there is nothing in common between DNS and SEO, but you will be very wrong. Yes, the DNS and SEO are...
What is DNS propagation? How to check DNS propagation?
In this article we’ll talk about DNS Propagation. But before that, we need to make sure you know...