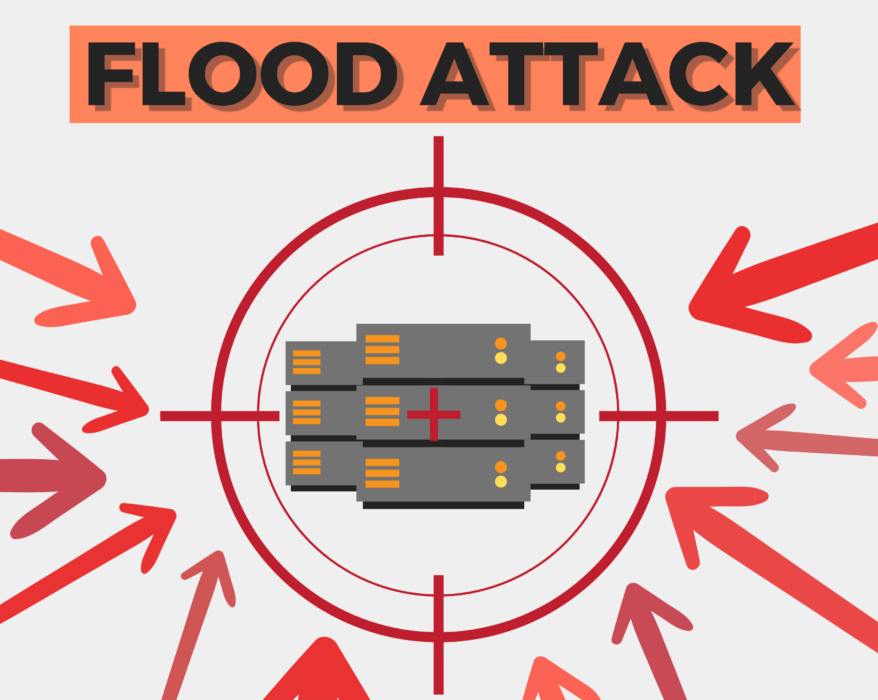
Flood Attack: Prevention and Protection
In today’s digital age, security breaches and cyberattacks have become increasingly common....
Understanding BGP: A Comprehensive Guide for Beginners
Border Gateway Protocol (BGP) plays a crucial role in directing data between different networks. If you’re new to the topic,...
Getting Started with DNS Prefetch on Your Website
In the ever-competitive landscape of web performance, milliseconds matter. Whether you’re optimizing for Core Web Vitals, reducing...
What is Microsoft Azure? IaaS, PaaS, and SaaS.
Before we start talking about Microsoft Azure, let’s see why such a service exists. It the modern...
R.U.D.Y. (R U Dead Yet) Attack Explained
In the ever-evolving landscape of cybersecurity, new threats constantly emerge, challenging the robustness of online systems. One such...
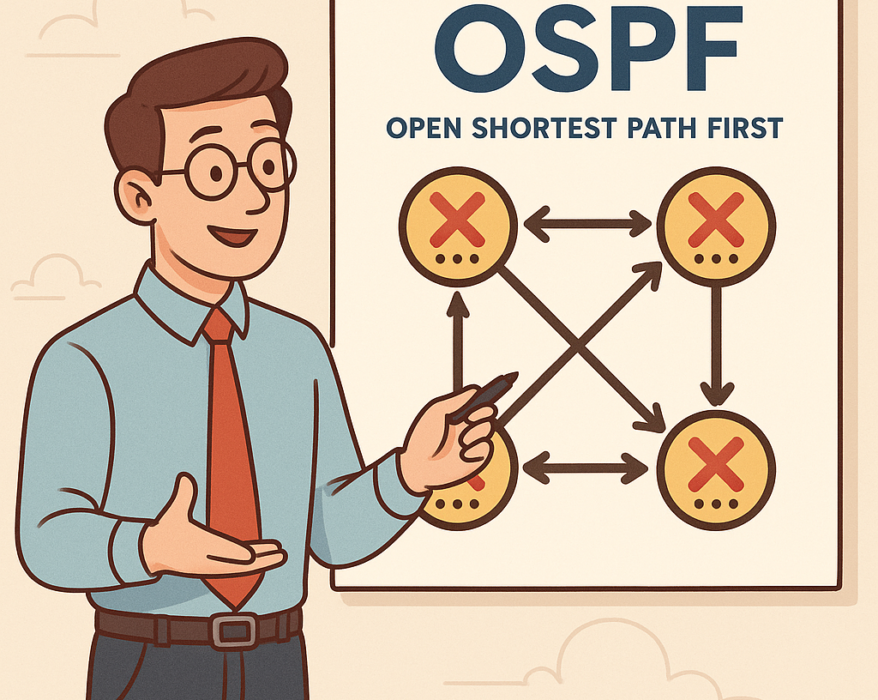
OSPF (Open Shortest Path First): What It Is and How It Works
OSPF (Open Shortest Path First) is one of the most widely used routing protocols in modern IP...
Magento, is it a good e-commerce platform?
Choosing the right e-commerce platform is one of the most important decisions any online retailer will make. With the continued rise of...
Email forwards – what are they and how to use them?
Can you guess what email forwards do? Yes, it is very simple, they redirect emails from one mailbox to another. Just as you can forward...
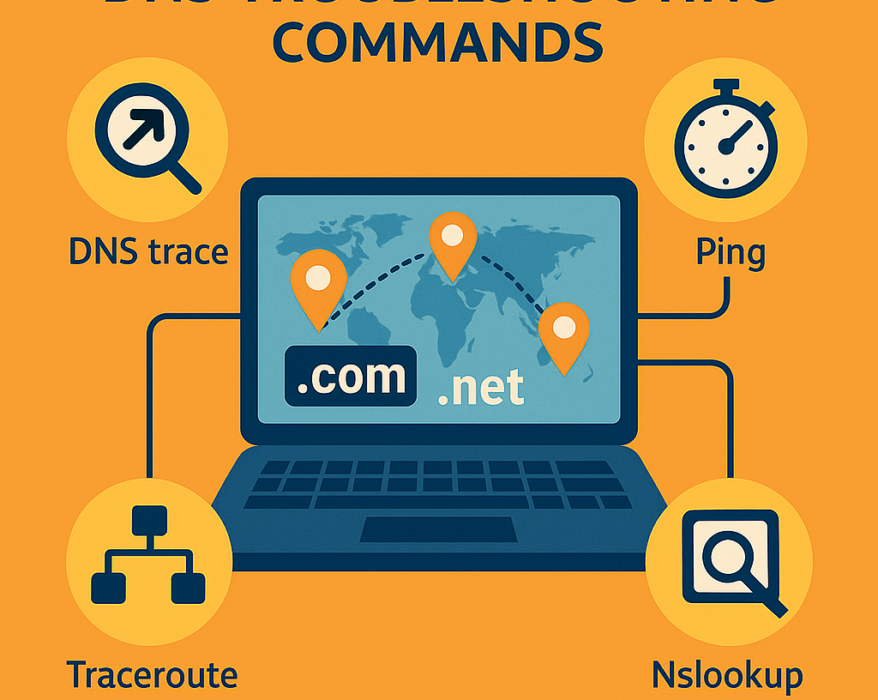
Тools – DNS trace, Ping, Traceroute, Nslookup, Reverse lookup
Navigating the world of DNS and network management can often feel like a complex puzzle, especially...